-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
Troubleshooting Site to Site VPN in Aggressive Mode with multiple Dynamic WAN connections.



Description
Customer is using 2 WAN connection on Site A (WAN X1 – 81.148.71.71 PPPOE (Dynamic) and WAN X2 – 109.176.181.170 static)
and X2 is being used as the primary WAN connection; On Site B,X2 WAN IP: 109.176.181.170 has been setup as the primary gateway for VPN tunnel,Secondary gateway is WAN X1 – 81.148.71.71 PPPOE (Dynamic) . Tunnel doesn’t come up when is X2 is down it's not picking up X1 IP.
(use screenshot from this article:https://www.sonicwall.com/support/knowledge-base/configuring-aggressive-mode-site-to-site-vpn-when-a-site-has-dynamic-wan-public-ip-address/170505565649605/)
Resolution
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
- Navigate to Network | IPsec VPN | Rules and Settings page and Click Edit button of the specific policy .
- The VPN Policy window is displayed , Click on the Advanced tab .
- Select the VPN bound to option.
- Select Interface X2 (3.3.3.3) as the Primary gateway as Site B is set as the same IP – 3.3.3.3.
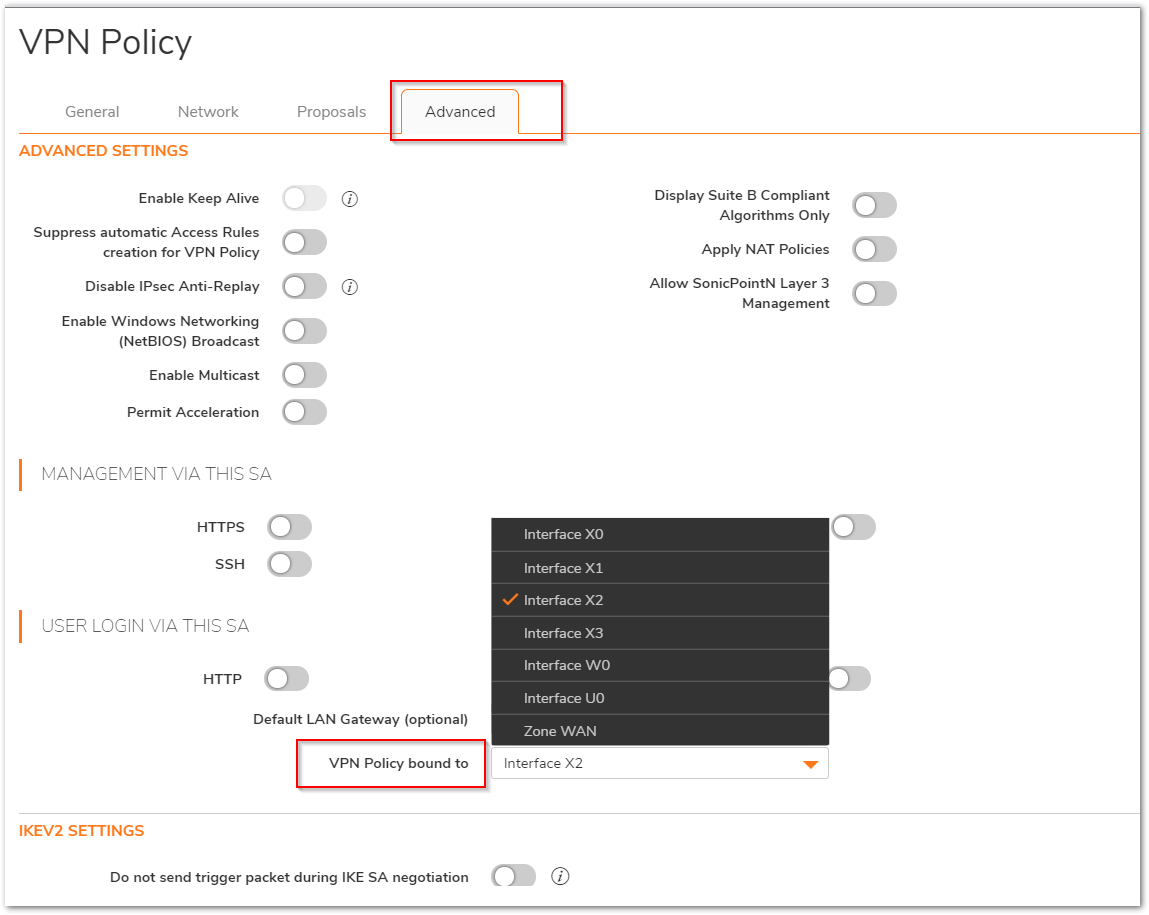
 NOTE: By default, VPN policy bound to option is set to zone WAN where VPN tunnel will be established with Primary WAN as configured in Failover/Load balancing . If we want to establish the tunnel from a specific WAN interface please select the interface under VPN Policy bound to where we have 2 WAN connection (ie) Site A in this scenario.
NOTE: By default, VPN policy bound to option is set to zone WAN where VPN tunnel will be established with Primary WAN as configured in Failover/Load balancing . If we want to establish the tunnel from a specific WAN interface please select the interface under VPN Policy bound to where we have 2 WAN connection (ie) Site A in this scenario. - If the tunnel does not negotiate successfully, check the SonicWall’s log on the Monitor |Logs |System Logs page to see if there are any error messages for VPN negotiation. If the tunnel is not negotiating and there are error messages displayed, go over the settings on both side to make sure that they match and attempt to bring the tunnel up again.
- You should see the active VPN tunnel listed on the remote site, and the tunnel has negotiated with the Primary IPsec gateway. If the tunnel does not negotiate successfully, check the SonicWall’s log on the Monitor |Logs |System Logs page to see if there are any error messages for VPN negotiation. If the tunnel is not negotiating and there are error messages displayed, go over the settings on both side to make sure that they match and attempt to bring the tunnel up again.
How to Test this Scenario:
Try to ping an IP address from Site A to Site B or Vice Versa.
- Before receiving successful replies, you might see couple of Request Timed Out messages while the VPN tunnel is still establishing.
For Troubleshooting Articles, please see Related Items section below:
Main Mode - https://www.sonicwall.com/en-us/support/knowledge-base/170504380887908
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
- Navigate to Manage | VPN | Base Settings page and Click Edit button of the specific policy .
- The VPN Policy window is displayed , Click on the Advanced tab .
- Select the VPN bound to option.
- Select Interface X2 (3.3.3.3) as the Primary gateway as Site B is set as the same IP – 3.3.3.3.
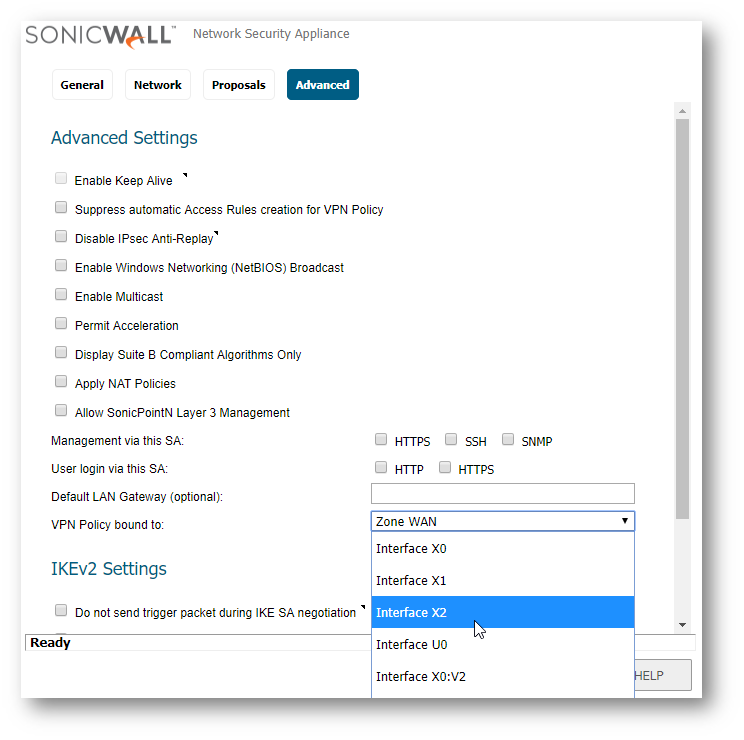
 NOTE: By default, VPN policy bound to option is set to zone WAN where VPN tunnel will be established with Primary WAN as configured in Failover/Load balancing . If we want to establish the tunnel from a specific WAN interface please select the interface under VPN Policy bound to where we have 2 WAN connection (ie) Site A in this scenario.
NOTE: By default, VPN policy bound to option is set to zone WAN where VPN tunnel will be established with Primary WAN as configured in Failover/Load balancing . If we want to establish the tunnel from a specific WAN interface please select the interface under VPN Policy bound to where we have 2 WAN connection (ie) Site A in this scenario. - If the tunnel does not negotiate successfully, check the SonicWall’s log on the Log | View page to see if there are any error messages for VPN negotiation. If the tunnel is not negotiating and there are error messages displayed, go over the settings on both side to make sure that they match and attempt to bring the tunnel up again.
- You should see the active VPN tunnel listed on the remote site, and the tunnel has negotiated with the Primary IPsec gateway. If the tunnel does not negotiate successfully, check the SonicWall’s log on the ‘Log | View’ page to see if there are any error messages for VPN negotiation. If the tunnel is not negotiating and there are error messages displayed, go over the settings on both side to make sure that they match and attempt to bring the tunnel up again.
How to Test this Scenario
Try to ping an IP address from Site A to Site B or Vice Versa.
- Before receiving successful replies, you might see couple of “Request Timed Out“ messages while the VPN tunnel is still establishing.
For Troubleshooting Articles, please see Related Items section below:
Main Mode - How Can I Configure A Site To Site VPN Policy Using Main Mode?
Resolution for SonicOS 6.2 and Below
The below resolution is for customers using SonicOS 6.2 and earlier firmware. For firewalls that are generation 6 and newer we suggest to upgrade to the latest general release of SonicOS 6.5 firmware.
- Navigate to VPN | Settings page and Click Edit button of the specific policy .
- The VPN Policy window is displayed , Click the Advanced tab .
- Select the VPN bound to option.
- Select Interface X2 (3.3.3.3) as the Primary gateway as Site B is set as the same IP – 3.3.3.3.

 NOTE: By default, VPN policy bound to option is set to zone WAN where VPN tunnel will be established with Primary WAN as configured in Failover/Load balancing . If we want to establish the tunnel from a specific WAN interface please select the interface under VPN Policy bound to where we have 2 WAN connection (ie) Site A in this scenario.
NOTE: By default, VPN policy bound to option is set to zone WAN where VPN tunnel will be established with Primary WAN as configured in Failover/Load balancing . If we want to establish the tunnel from a specific WAN interface please select the interface under VPN Policy bound to where we have 2 WAN connection (ie) Site A in this scenario. - If the tunnel does not negotiate successfully, check the SonicWall’s log on the Log | View page to see if there are any error messages for VPN negotiation. If the tunnel is not negotiating and there are error messages displayed, go over the settings on both side to make sure that they match and attempt to bring the tunnel up again.
- You should see the active VPN tunnel listed on the remote site, and the tunnel has negotiated with the Primary IPSec gateway. If the tunnel does not negotiate successfully, check the SonicWall’s log on the Log | View page to see if there are any error messages for VPN negotiation. If the tunnel is not negotiating and there are error messages displayed, go over the settings on both side to make sure that they match and attempt to bring the tunnel up again.
How to Test this Scenario:
Try to ping an IP address from Site A to Site B or Vice Versa.
- Before receiving successful replies, you might see couple of Request Timed Out messages while the VPN tunnel is still establishing.
 EXAMPLE: For Troubleshooting Articles, see related items section below:
EXAMPLE: For Troubleshooting Articles, see related items section below:
Main Mode - How Can I Configure A Site To Site VPN Policy Using Main Mode?
Related Articles
- Error:"Invalid API Argument" when modifying the access rules
- Cysurance Partner FAQ
- Configure probe monitoring for WAN Failover and Loadbalancing - SonicWall UTM
Categories
- Firewalls > NSa Series > VPN
- Firewalls > NSv Series > VPN
- Firewalls > TZ Series > VPN






 YES
YES NO
NO