PDF campaign distributing Ursnif through malicious VBS

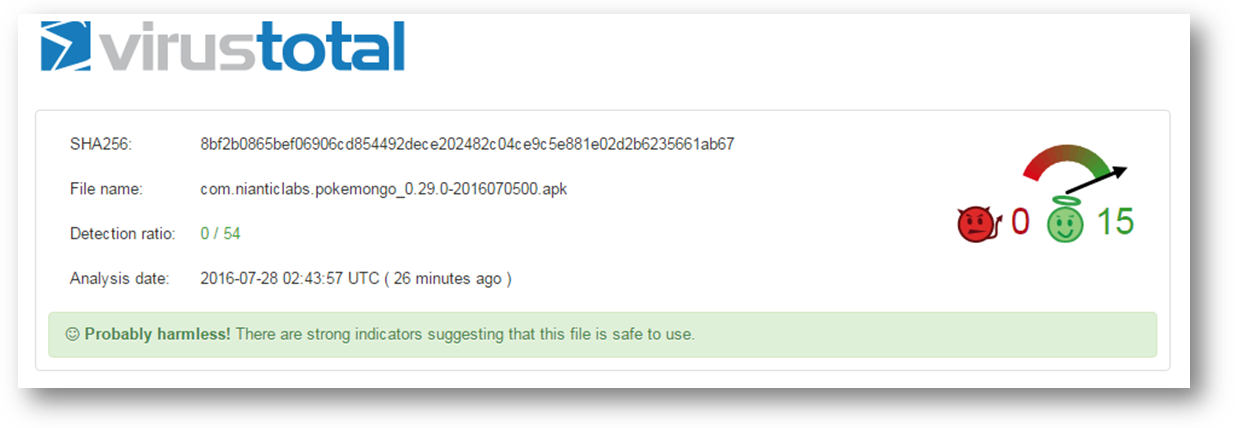
SonicWall RTDMI engine detected a number of PDF files containing link to malicious archive file. The non-existence of this malicious file at the time of detection in popular malware search portals like the VirusTotal and the Reversing Labs indicates the effectiveness of the RTDMI engine.
Fig-1 VirusTotal results for the PDF file
Analysis
PDF file are being distributed to victims, disguised as a document from Australian Organizations like Indigenous Business Australia etc. To deceive victims, PDF file is made to look as realistic as possible by having misleading text and icons related to the organization whose users would be targeted. The document file displays an icon showing the victim that a document file would be downloaded on clicking the icon, as shown in the images below. Rather an archive containing malicious VBScript is downloaded from “hxxp://kruanchan.com/00198728883.zip”.
Fig-2 Snapshots of PDF files.
At the time of analysis, both the archive and the malicious VBScript have detection from a handful of AV Vendors as could be seen below:
Fig-3 VirusTotal results for the downloaded archive file
Fig-4 VirusTotal results for the VBS script file
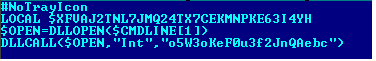
To hinder analysis, the VBScript is highly obfuscated as shown below:
Fig-5: Obfuscated VBScript code
Fig-6 Code of VBScript after deobfuscation
It could be seen above, the script first creates an Internet shortcut file named “Google.url” in the %TEMP% directory, having ‘www.google.com’ as the target link. Then it tries to download malicious content from “hxxp://news.pompeox.org/”, save it in the %TEMP% folder as “ie.exe”, finally executes the downloaded file. The downloaded file belongs to Ursnif malware family.
Indicators of Compromise:
PDF:
0a2f235f05f376fcf150fda15229b070dec2018cb944b1bd0d9a4e25b5bdcf93
27ea0ef04a082aa7a48f48d4197b9039eeadd4b01eb6c285581acdcc436d5d9c
3a22b101a3af813080be8aaeb73583eef5f4683363330cd6a0342efee1282b7b
3e96c3c6829cd3fc3b79c9407321f832ff30d372a350e5eead67a907c188f814
97992932e1651273168da68bfbbe7ed50a02e5829ccdfde9543faeb83020835d
b3da4bbdc7e6da8111eff84051f0c91da2424905e7ea81facd8f3ceba01e1222
e9fc167781608914489c500ed5445c27db0b3e216a7917c2c9b88269ba864b6c
Archive: ab74a5181b552055621e1abbd0336a1d7f110360db20ab8e51f97a332d4024e3
VBS: 554da6d32b3226bfe058fa545be80dc06895cca33843bf618c7c65a5e14d47b4
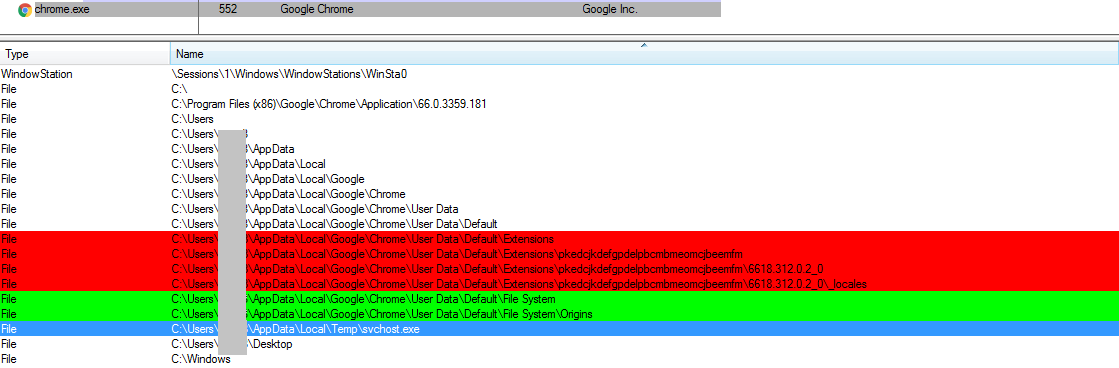
Fig-7 Snapshot of SMASH detection Report
Share This Article

An Article By
An Article By
Security News
Security News