Microsoft Security Bulletin Coverage for June 2024

Overview
Microsoft’s June 2024 Patch Tuesday has 49 vulnerabilities, 24 of which are Elevation of Privilege. The SonicWall Capture Labs threat research team has analyzed and addressed Microsoft’s security advisories for the month of June 2024 and has produced coverage for seven of the reported vulnerabilities.
Vulnerabilities with Detections
| CVE | CVE Title | Signature |
| CVE-2024-30080 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability | IPS 4452 Microsoft Message Queuing RCE (CVE-2024-30080) |
| CVE-2024-30084 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability | ASPY 6802 Exploit-exe exe.MP_391 |
| CVE-2024-30087 | Win32k Elevation of Privilege Vulnerability | ASPY 6805 Exploit-exe exe.MP_392 |
| CVE-2024-30088 | Windows Kernel Elevation of Privilege Vulnerability | ASPY 6806 Exploit-exe exe.MP_393 |
| CVE-2024-30089 | Microsoft Streaming Service Elevation of Privilege Vulnerability | ASPY 581 Exploit-exe exe.MP_390 |
| CVE-2024-30091 | Win32k Elevation of Privilege Vulnerability | ASPY 580 Exploit-exe exe.MP_389 |
| CVE-2024-35250 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability | ASPY 579 Exploit-exe exe.MP_388 |
Release Breakdown
The vulnerabilities can be classified into the following categories:
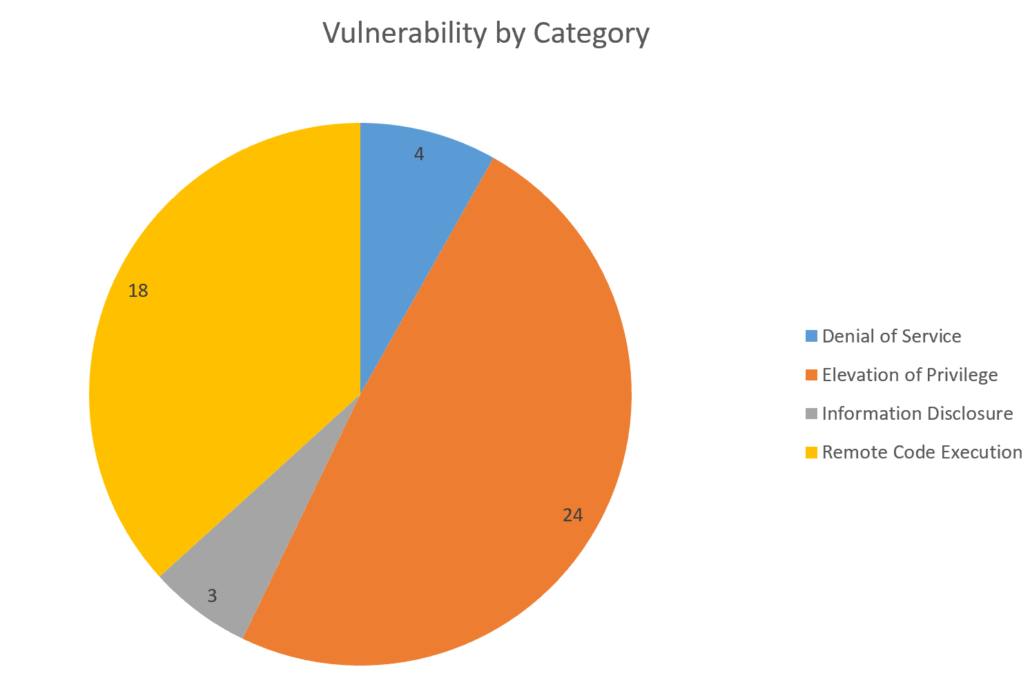
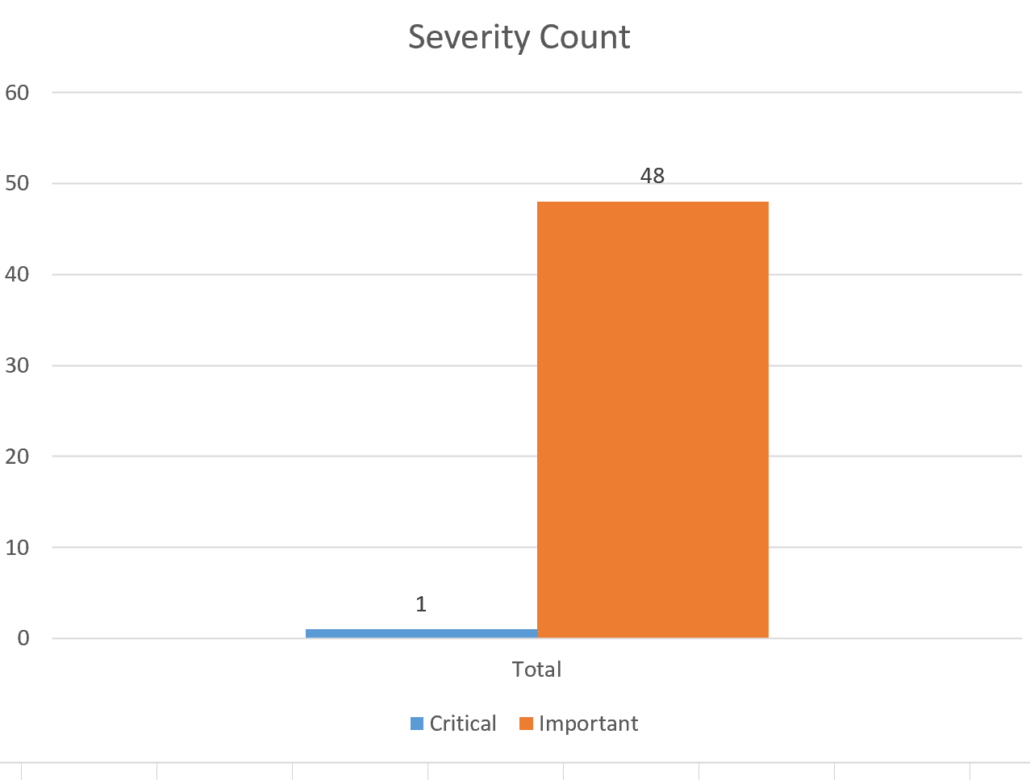
For June there is one Critical, 48 Important and zero Moderate vulnerabilities.
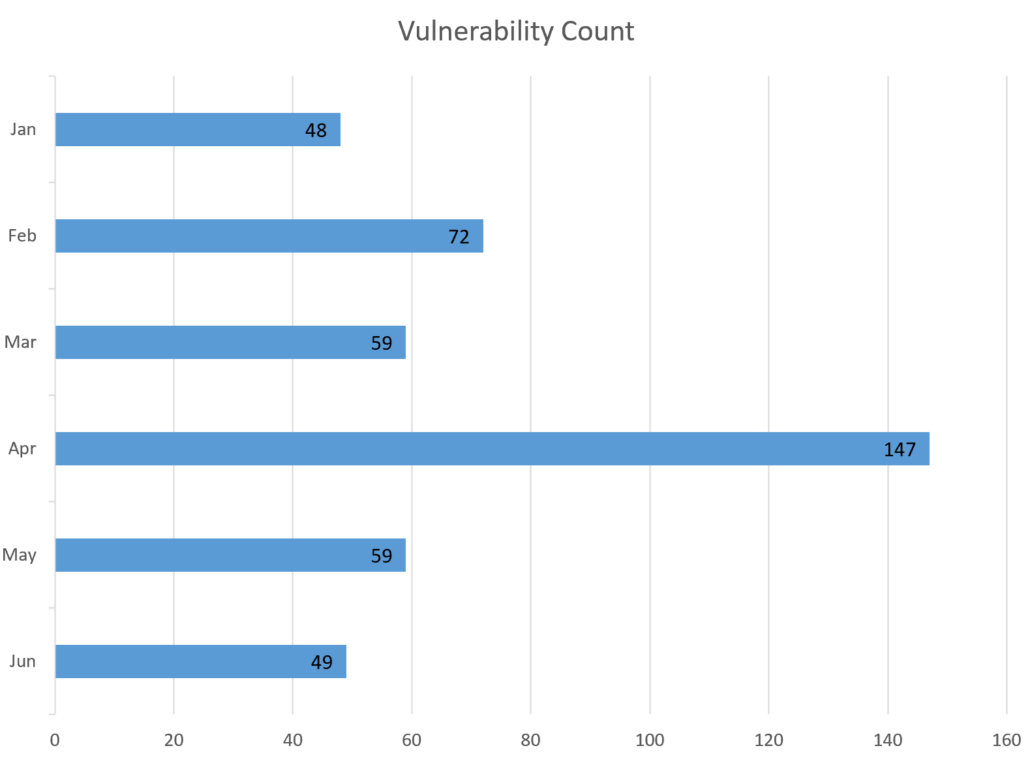
2024 Patch Tuesday Monthly Comparison
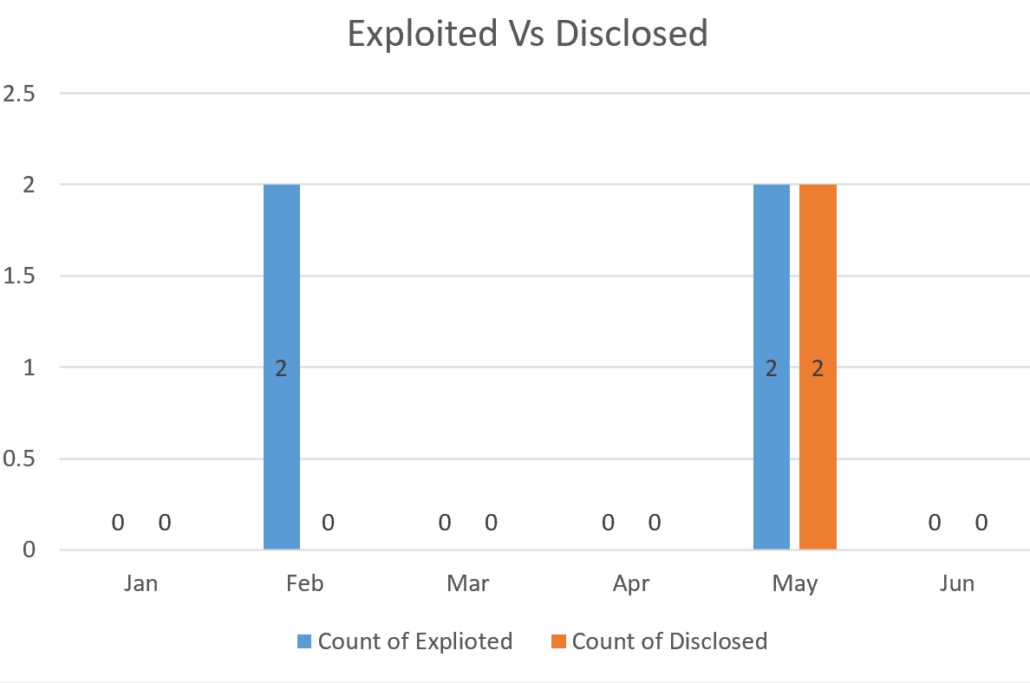
Microsoft tracks vulnerabilities that are being actively exploited at the time of discovery and those that have been disclosed publicly before the Patch Tuesday release for each month. The above chart displays these metrics as seen each month.
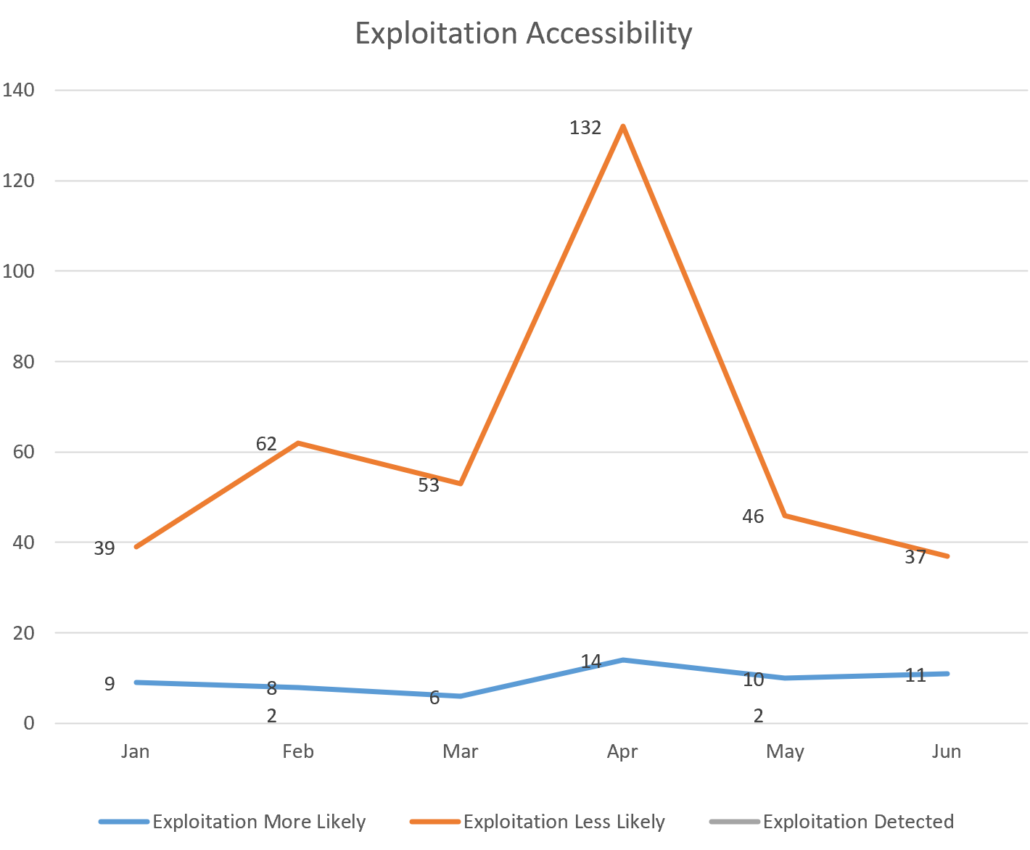
Release Detailed Breakdown
Denial of Service Vulnerabilities
| CVE-2024-30065 | Windows Themes Denial of Service Vulnerability |
| CVE-2024-30070 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2024-30083 | Windows Standards-Based Storage Management Service Denial of Service Vulnerability |
| CVE-2024-35252 | Azure Storage Movement Client Library Denial of Service Vulnerability |
Elevation of Privilege Vulnerabilities
| CVE-2024-29060 | Visual Studio Elevation of Privilege Vulnerability |
| CVE-2024-30064 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30066 | Winlogon Elevation of Privilege Vulnerability |
| CVE-2024-30067 | WinLogon Elevation of Privilege Vulnerability |
| CVE-2024-30068 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30076 | Windows Container Manager Service Elevation of Privilege Vulnerability |
| CVE-2024-30082 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30084 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-30085 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-30086 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-30087 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30088 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30089 | Microsoft Streaming Service Elevation of Privilege Vulnerability |
| CVE-2024-30090 | Microsoft Streaming Service Elevation of Privilege Vulnerability |
| CVE-2024-30091 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30093 | Windows Storage Elevation of Privilege Vulnerability |
| CVE-2024-30099 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-35248 | Microsoft Dynamics 365 Business Central Elevation of Privilege Vulnerability |
| CVE-2024-35250 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-35253 | Microsoft Azure File Sync Elevation of Privilege Vulnerability |
| CVE-2024-35254 | Azure Monitor Agent Elevation of Privilege Vulnerability |
| CVE-2024-35255 | Azure Identity Libraries and Microsoft Authentication Library Elevation of Privilege Vulnerability |
| CVE-2024-35265 | Windows Perception Service Elevation of Privilege Vulnerability |
| CVE-2024-37325 | Azure Science Virtual Machine (DSVM) Elevation of Privilege Vulnerability |
Information Disclosure Vulnerabilities
| CVE-2024-30069 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-30096 | Windows Cryptographic Services Information Disclosure Vulnerability |
| CVE-2024-35263 | Microsoft Dynamics 365 (On-Premises) Information Disclosure Vulnerability |
Remote Code Execution Vulnerabilities
| CVE-2024-30052 | Visual Studio Remote Code Execution Vulnerability |
| CVE-2024-30062 | Windows Standards-Based Storage Management Service Remote Code Execution Vulnerability |
| CVE-2024-30063 | Windows Distributed File System (DFS) Remote Code Execution Vulnerability |
| CVE-2024-30072 | Microsoft Event Trace Log File Parsing Remote Code Execution Vulnerability |
| CVE-2024-30074 | Windows Link Layer Topology Discovery Protocol Remote Code Execution Vulnerability |
| CVE-2024-30075 | Windows Link Layer Topology Discovery Protocol Remote Code Execution Vulnerability |
| CVE-2024-30077 | Windows OLE Remote Code Execution Vulnerability |
| CVE-2024-30078 | Windows Wi-Fi Driver Remote Code Execution Vulnerability |
| CVE-2024-30080 | Microsoft Message Queuing (MSMQ) Remote Code Execution Vulnerability |
| CVE-2024-30094 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30095 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30097 | Microsoft Speech Application Programming Interface (SAPI) Remote Code Execution Vulnerability |
| CVE-2024-30100 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| CVE-2024-30101 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-30102 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2024-30103 | Microsoft Outlook Remote Code Execution Vulnerability |
Share This Article

An Article By
An Article By
Security News
Security News