LucKY_Gh0$t Ransomware Operator Demands $220 for Decryption

The SonicWall Capture Labs threat research team has been tracking recently released ransomware known as LucKY_Gho$t. This ransomware is based on the popular Chaos ransomware. During our analysis, we were able to have a conversation with the operator, who states that $220 in Bitcoin is required for file retrieval.
Infection Cycle
The malware uses the following icon:

Figure 1: Malware icon
Upon infection, the malware encrypts files on the system and appends 4 alphanumeric characters to their filenames. It changes the desktop background to the following image:

Figure 2: Desktop image
read_it.txt is written to all directories containing encrypted files. It contains the following message:
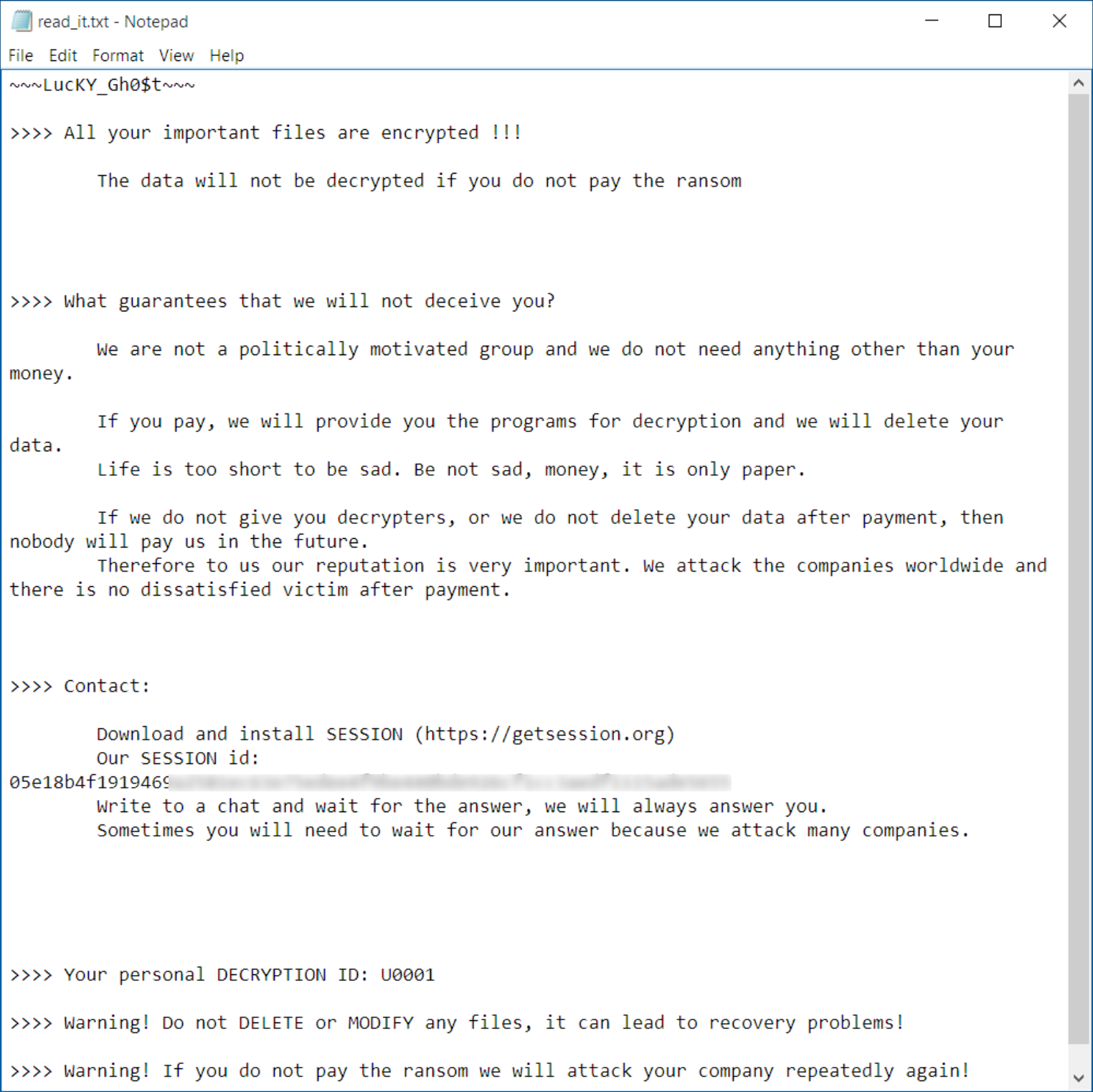
Figure 3: Ransom note
The following targeted file types were found in the decompiled malware code:
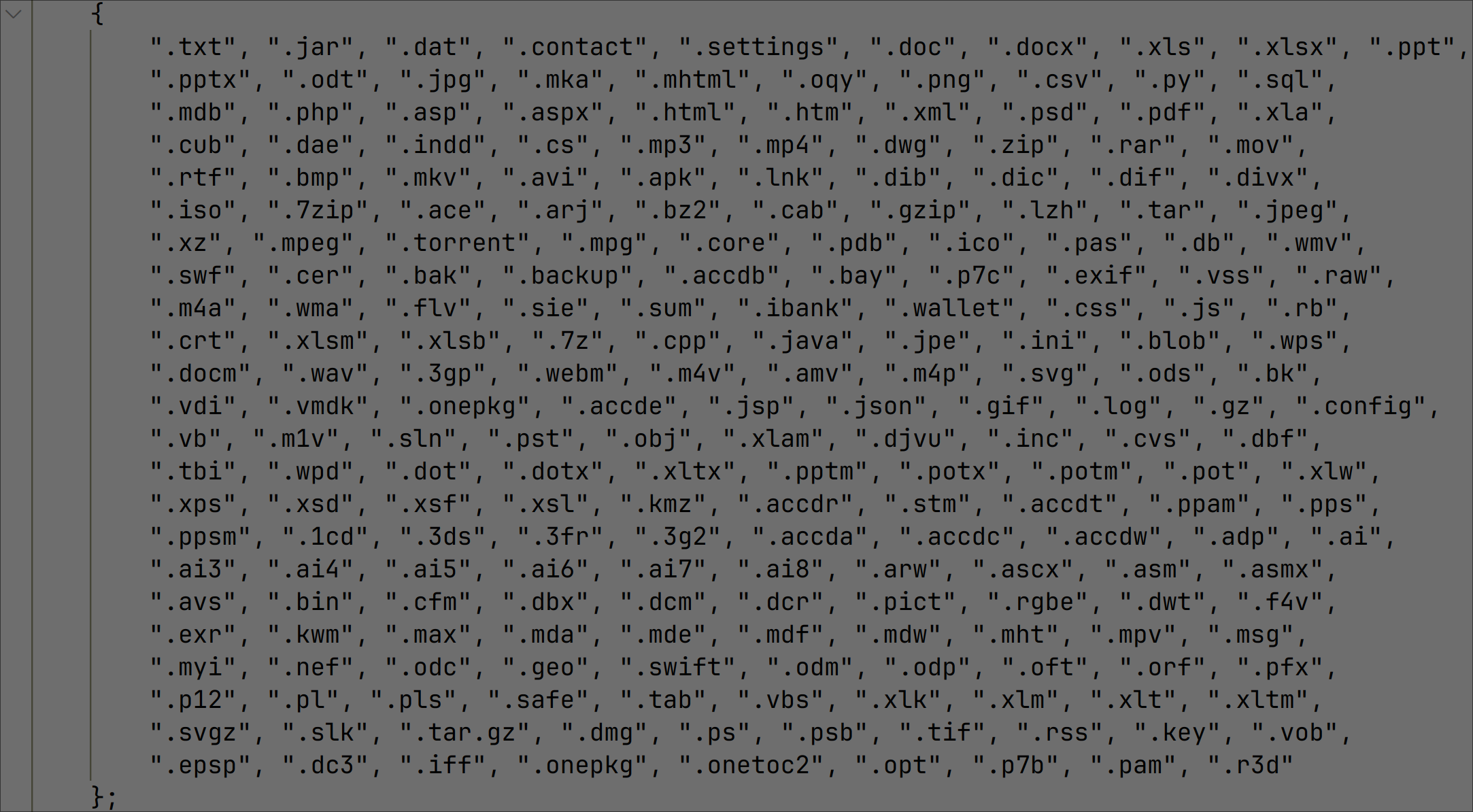
Figure 4: Targeted file types
The malware disables various system recovery features:
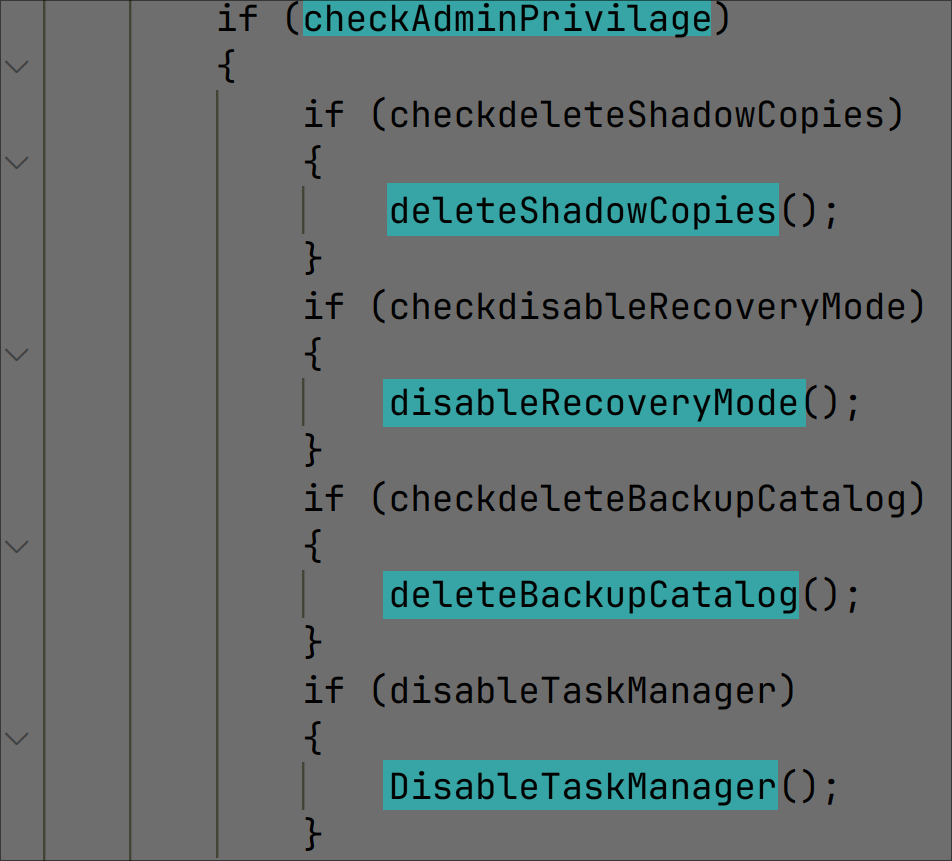
Figure 5: System recovery deactivation
We downloaded and installed the Session chat application as instructed in the ransom note. Session is an “end-to-end encrypted messenger that minimizes sensitive metadata, designed and built for people who want absolute privacy and freedom from any form of surveillance”. After a long wait, we had the following conversation with the ransomware operator:
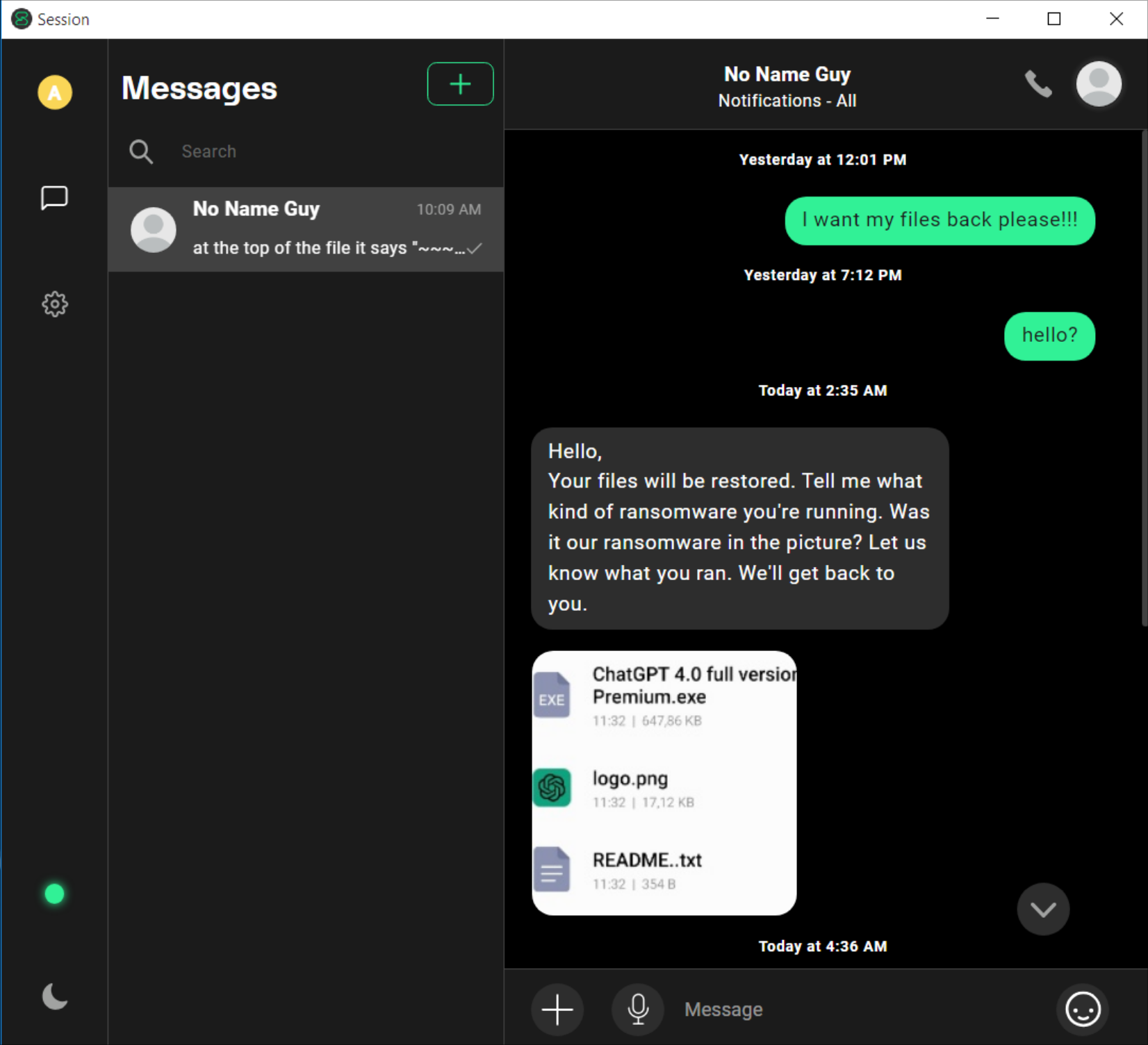
Figure 6: Conversation with operator
A decrypter tool is offered:
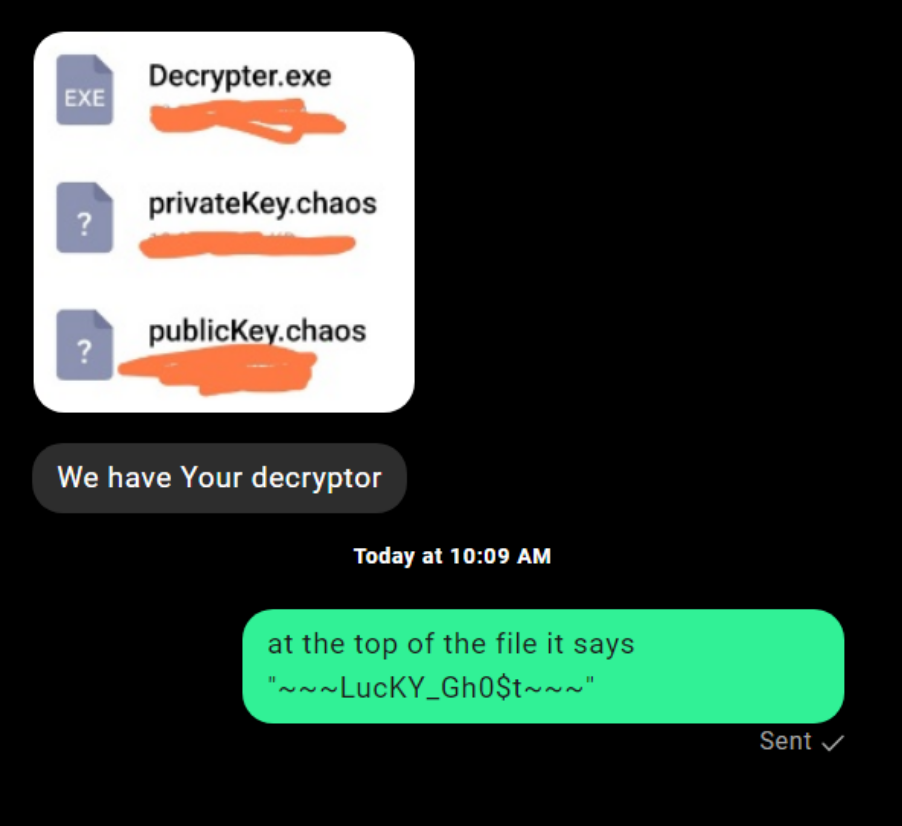
Figure 7: Conversation continued
$220 USD in Bitcoin is demanded for file retrieval:
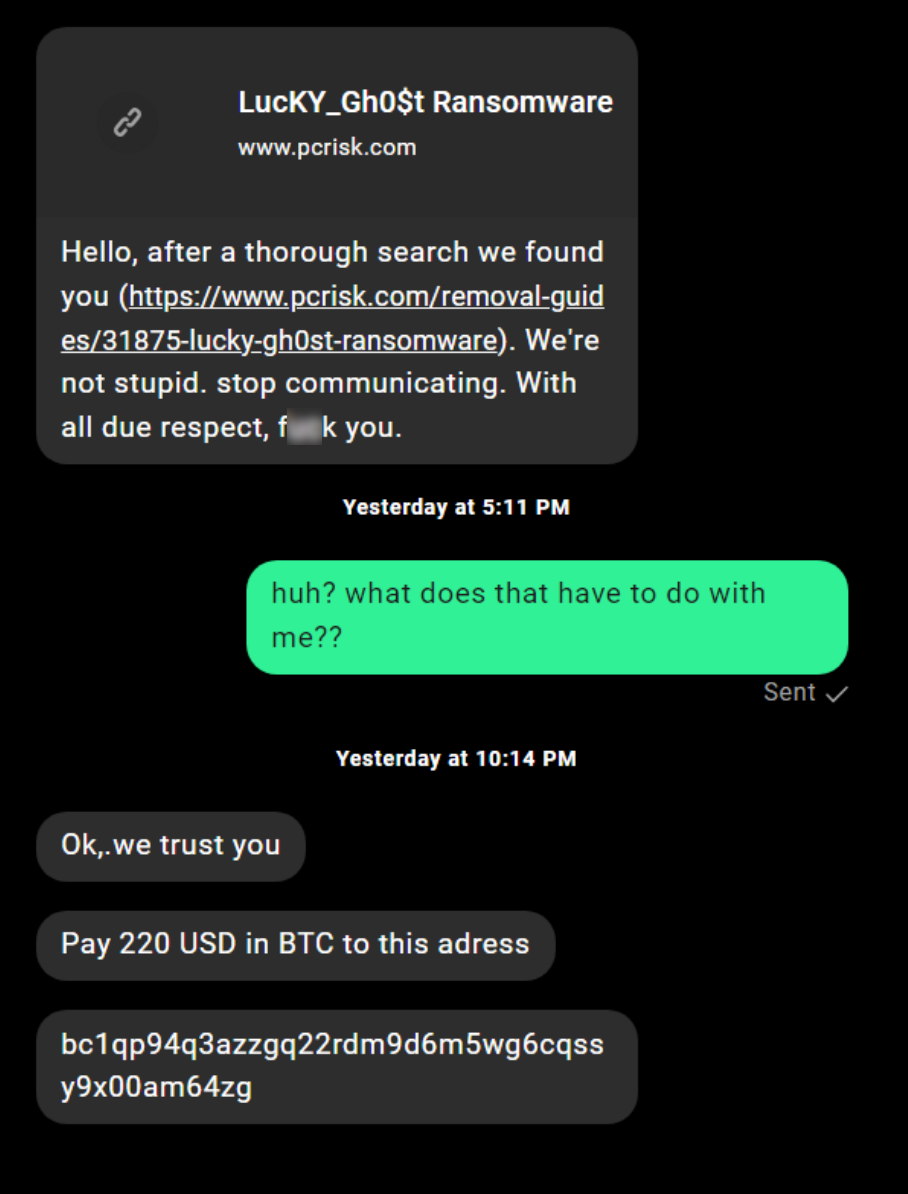
Figure 8: Ransom demand
SonicWall Capture Labs provides protection against this threat via the following signature:
• GAV: Luckyghost.RSM (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.
Share This Article

An Article By
An Article By
Security News
Security News
