Apache Struts Unauthorized Arbitrary File Upload

Overview
The SonicWall Capture Labs threat research team became aware of an unauthorized arbitrary file upload vulnerability in Apache Struts, assessed its impact and developed mitigation measures for the vulnerability. Apache Struts, an open-source MVC framework to develop modern web applications based on Java, has released versions 2.5.33 and 6.3.0.2 addressing this issue which is affecting the following versions of Struts: Struts 2.0.0 - Struts 2.3.37 (EOL), Struts 2.5.0 - Struts 2.5.32, and Struts 6.0.0 - Struts 6.3.0. Since Apache Struts has historically been a luring target among threat actors due to its widespread usage, this vulnerability has already started being exploited in the wild. This could be easily anticipated considering its ease of exploitation as well as existence of public POC. Due to active exploitation, we strongly recommend upgrading to the latest version of Struts.
CVE Details
This vulnerability has been assigned the Common Vulnerabilities and Exposures (CVE) identifier CVE-2023-50164.
The overall CVSS score is 9.8 (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H).
Base score is 9.8 (AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H), based on the following metrics:
- Attack vector is network.
- Attack complexity is low.
- Privileges required is none.
- User interaction is none.
- Scope is unchanged.
- Impact of this vulnerability on data confidentiality is high.
- Impact of this vulnerability on data integrity is high.
- Impact of this vulnerability on data availability is high.
Technical Overview
This vulnerability allows the threat actors to upload an arbitrary file in the webroot of the tomcat web server through a POST request. This flaw allows the attacker to not only tamper with the file upload parameters but also to append an additional parameter, which allows the threat actor to upload a file at any location. The implemented sanitization is inadequate to prevent parameter pollution. Changing the case of parameters to lowercase can override the file name variable uploadFileName allowing path traversal and leading to compromise of the system.
To remediate the issue, Apache Struts has released a patch as commits 162e29f and d8c6969 for versions 2.5.x and 6.3.x respectively. A closer look at the patch confirms the improvements in the functions get, contains and remove by making them case insensitive to prevent unique consideration of manipulated parameters based on case sensitivity as seen in Figure 1 for the function get.
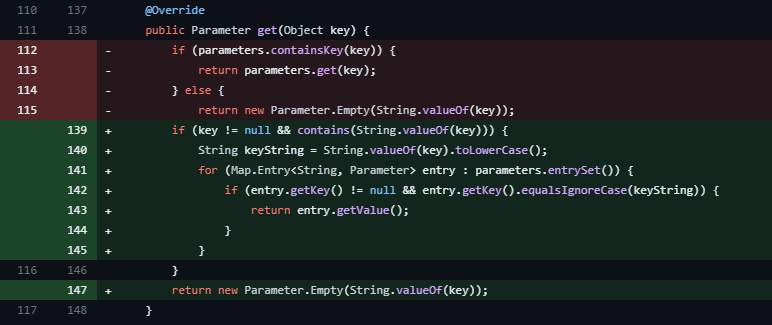
Figure 1: Improved case-insensitive get function
Additionally, the function appendAll is improved to append all the parameters in a case-insensitive way to deny the overriding attempt of existing parameters as seen in Figure 2.
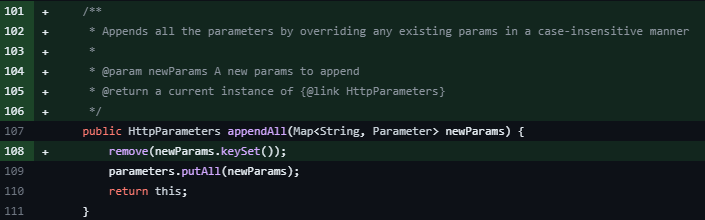
Figure 2: Improved appendAll function
Triggering the Vulnerability
This vulnerability can be triggered using a specially crafted POST request which contains a parameter with name=”Upload” (or uPLoad or uploaD) instead of the default value upload and the additional uploadFileName parameter that will override the path where the file will be saved as well as the name of the file as seen in Figure 3.
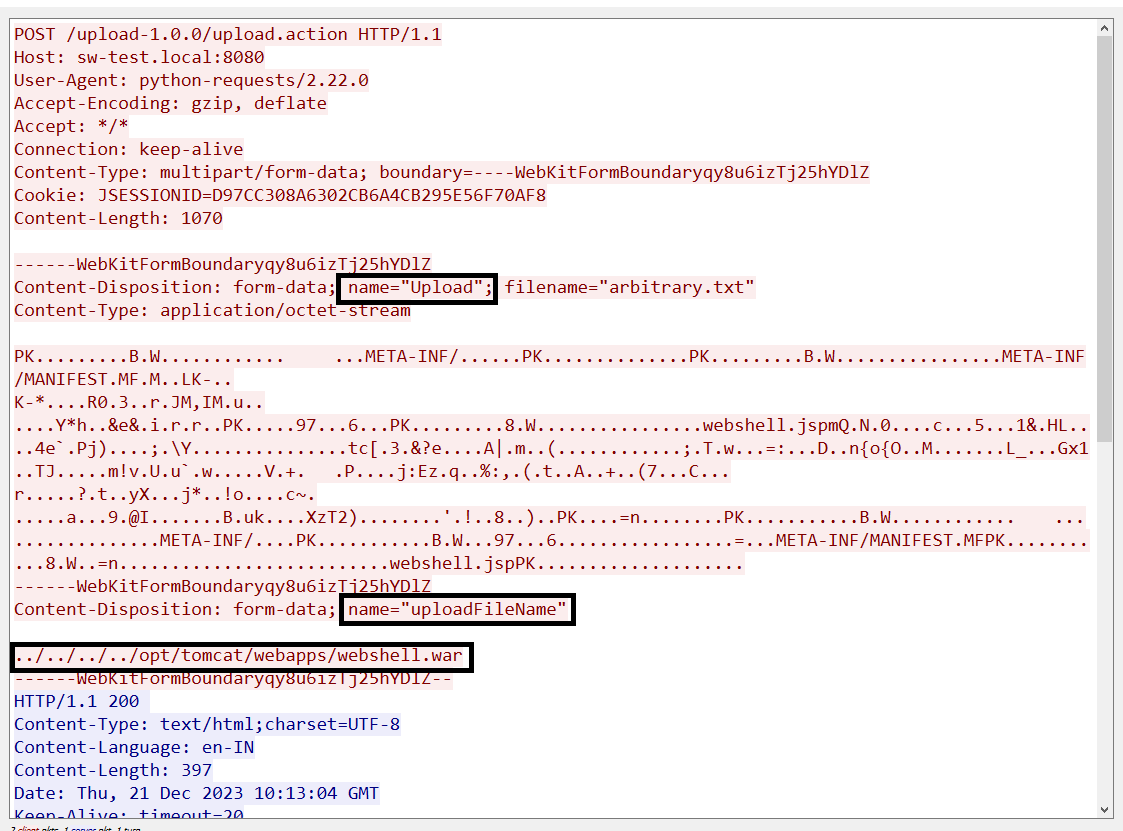
Figure 3: Malicious exploitation request
Exploitation
We used the publicly available PoC to analyze and understand the vulnerability and to set up a lab environment. The remote code execution in the vulnerable system is demonstrated by leveraging this vulnerability. The following video illustrates the uploading of a web shell and execution of the system command by sending a request, as seen in Figure 3 above.
SonicWall Protections
To ensure SonicWall customers are prepared for any exploitation that may occur due to this vulnerability, the following signature has been released:
- IPS:4194 Web Application Suspicious form-data 2
Additionally, a generic detection signature mentioned below is utilized to strengthen the protection.
- IPS:2764 Web Application Suspicious form-data 1
Threat Graph
SonicWall sensors have confirmed a spike in exploitation attempts of this vulnerability and a surge in exploitation attempts is expected in upcoming days considering the popularity of the software.
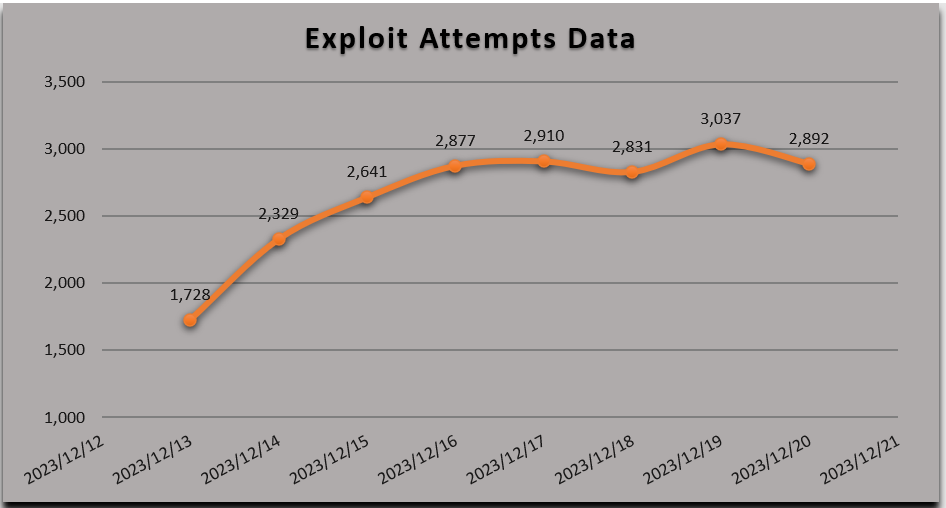
Figure 4: SonicWall signature hits data
Remediation Recommendations
Apache Struts has released an update to address the issue, and it is strongly recommended to update the application to the version 2.5.33 or 6.3.0.2 or newer as appropriate.
Relevant Links
Share This Article

An Article By
An Article By
Security News
Security News