Amadey Malware Has Improved Its String Decoding Algorithm

OVERVIEW
SonicWall Capture Labs Research team recently observed a new variant of Amadey malware. Amadey is a botnet with main objective of stealing sensitive information and to inject additional payload by receiving the commands from command & control server. In this variant we observed that it has modified its string decoding algorithm.
In this blog post, we will discuss.
- Introduction to Amadey malware.
- Command & control server communication.
- New string decoding algorithm.
INTRODUCTION
Since Amadey’s initial discovery in October 2018, the Amadey botnet has been operational. Amadey is mostly propagated by exploit kits like RigEK and Fallout EK. Amadey version found in current sample is 3.83.
Fig 1: Amadey CnC Login Panel
C2 COMMUNICATION
Malware starts collecting victim’s system information and initiate communication with CnC server by sending collected information. Victim’s System Information includes compute name, username, operating system, domain name, installed anti-virus vendor, system architecture and admin privilege present or not.
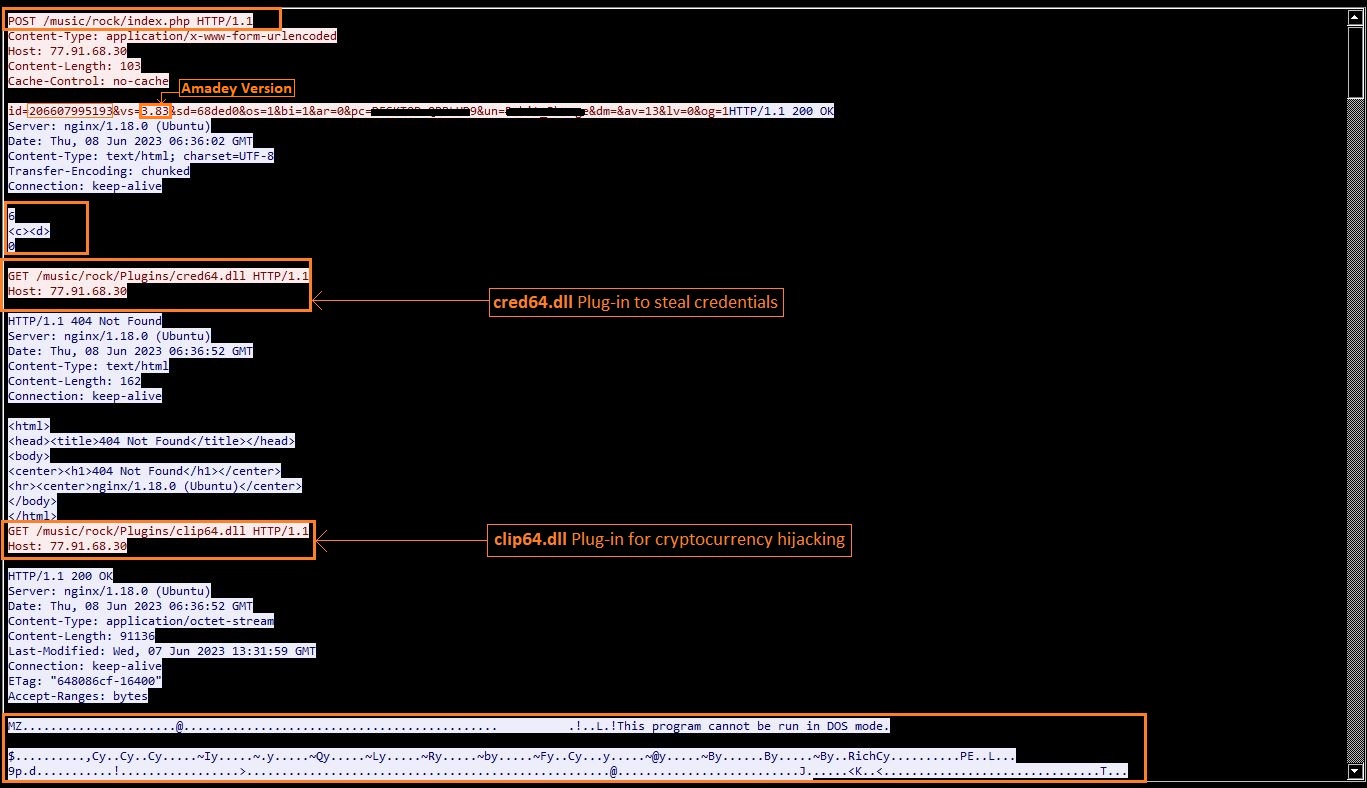
In response to send request, CnC can send URL to download additional malware. In this variant, it is seen distributing Redline stealer malware. Amadey sends requests to download two data stealing plugins of names cred.dll & clip64.dll.
Fig 2: Downloads add-on Plugins
STRINGS OBFUSCATION
Malware stores all the used strings like CNC domain address, AV product names, DLL file names, registry keys used for persistence, API names, URL parameters etc. Encoded strings are present in “.rdata” section of malware.
Fig 3: Some of Encoded Strings
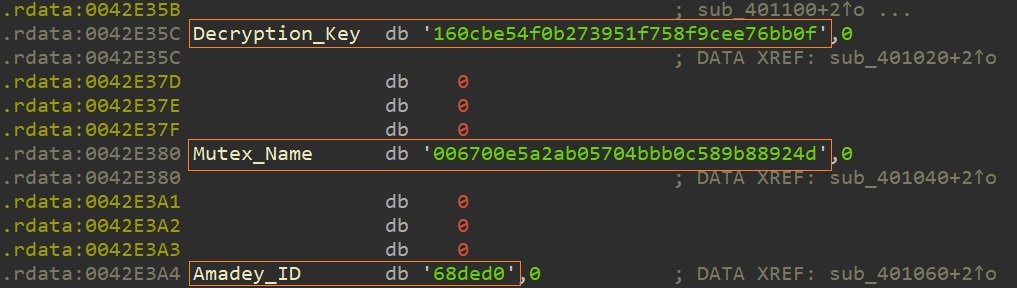
HARD CODED KEY
Fig 4: Hardcoded Decryption key, Mutex name, Amadey ID
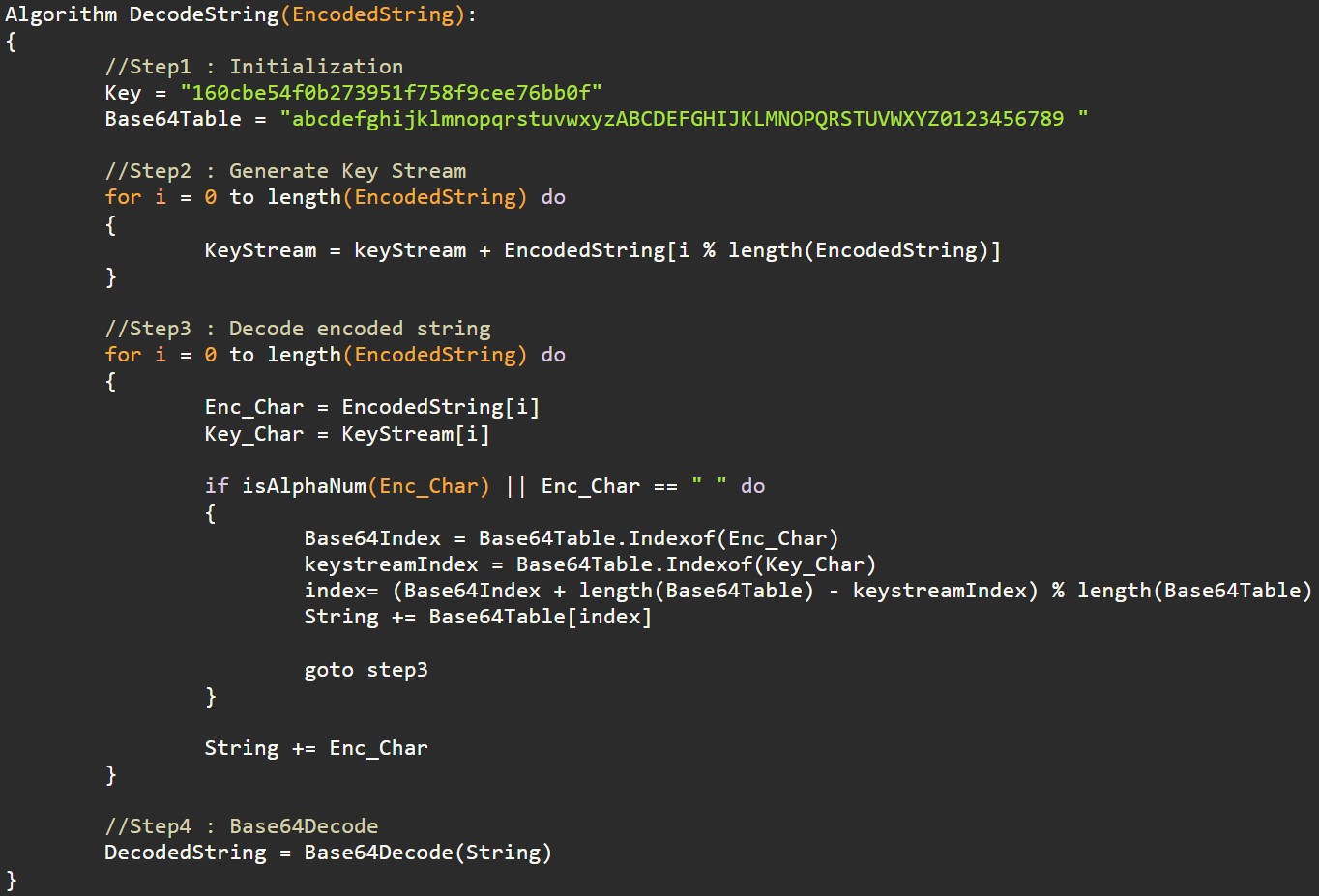
IMPROVED STRING ENCODING ALGORITHM
Fig 5: Pseudocode of string decoding algorithm
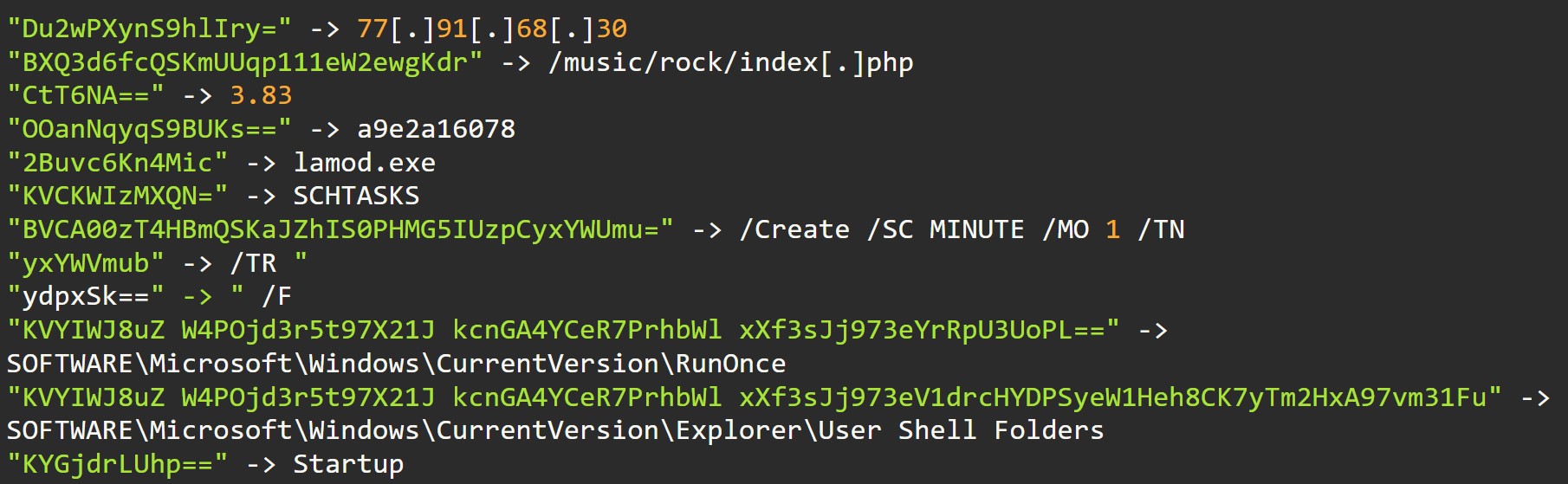
DECODED STRINGS
Fig 6: Some of Decoded strings
CONCLUSION
Amadey is botnet developed in C++ with main objective of stealing victims’ sensitive information. Amadey has capabilities to inject modules received from CnC which also makes it a downloader. Malware is using custom decoding algorithm to hide the strings.
SonicWall Capture Labs provides protection against this threat via the following signature:
- GAV: MalAgent.OLA_2 (Trojan)
This threat is also detected by SonicWall Capture ATP w/RTDMI and the Capture Client endpoint solutions.
IOC’s:
C2
hxxp://77[.]91[.]68[.]30/DSC01491/foto124[.]exe
hxxp://77[.]91[.]68[.]30/DSC01491/fotod25[.]exe
hxxp://77[.]91[.]68[.]30/music/rock/Plugins/clip64[.]dll
hxxp://77[.]91[.]68[.]30/music/rock/Plugins/cred32[.]dll
SHA256
dcda87129c5d1687d208553663943bde1fb19ca3942fccf99da672d4f6cb3fea -> Amadey Malware
5cfeac2fad035a1a351abd2d5734dcb858583fdbdb9cf7f9383f5c809593fe96 -> foto125.exe
a2f989a5f3fcfef29366f7f469c39636dc3505da5ad44953cdd58829813c1d6f -> foto124.exe
340c8464c2007ce3f80682e15dfafa4180b641d53c14201b929906b7b0284d87 -> cred64.dll
Share This Article

An Article By
An Article By
Security News
Security News