-
Products
-
SonicPlatform
SonicPlatform is the cybersecurity platform purpose-built for MSPs, making managing complex security environments among multiple tenants easy and streamlined.
Discover More
-
-
Solutions
-
Federal
Protect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn MoreFederalProtect Federal Agencies and Networks with scalable, purpose-built cybersecurity solutions
Learn More - Industries
- Use Cases
-
-
Partners
-
Partner Portal
Access to deal registration, MDF, sales and marketing tools, training and more
Learn MorePartner PortalAccess to deal registration, MDF, sales and marketing tools, training and more
Learn More - SonicWall Partners
- Partner Resources
-
-
Support
-
Support Portal
Find answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn MoreSupport PortalFind answers to your questions by searching across our knowledge base, community, technical documentation and video tutorials
Learn More - Support
- Resources
- Capture Labs
-
- Company
- Contact Us
How to allow certain websites on SonicOSX 7.0?



Description
SonicWall has an implicit deny rule which blocks all traffic. To allow a specific set of websites like google.com, we would need to add a security rule to appropriately allow them. Security rules consist of three sections, match criterion, action, and additional actions. We need to match the URLs to be allowed, allow access to them, and perform additional actions like showing the block page.
With most of the websites using HTTPS, we need to use DPI SSL so that we can easily filter them based on the full URI content. Without DPI SSL, we are dependent on the server name indicator or common name of the certificate presented to allow/deny a website.
Resolution
We would need to create the following to allow only certain websites through the firewall on SonicOSX 7.0.
- Creating a Decryption policy
- Creating Security Policies
 NOTE: On SonicOSX 7.0, the HTTPS content filtering is no longer present. So, if HTTPS websites are to be allowed, we need Client DPI SSL and a corresponding decryption policy to inspect them.
NOTE: On SonicOSX 7.0, the HTTPS content filtering is no longer present. So, if HTTPS websites are to be allowed, we need Client DPI SSL and a corresponding decryption policy to inspect them.
Creating a Decryption Policy:
Decryption policy matches the traffic and the only two action we can take are decrypt and bypass. With decryption, we get more visibility to the data helping us in performing better matches and applying the right security policy.
- Make sure that Client DPI SSL is enabled globally based on the KB: How to create a Decryption Policy on SonicOSX 7.0?
- Navigate to Policy | Rules and Policies | Decryption Policy tab and click on Top at the bottom of the screen. If you have multiple policies it is very important to choose the right priority to make sure that the decryption policy is getting applied to the necessary traffic.
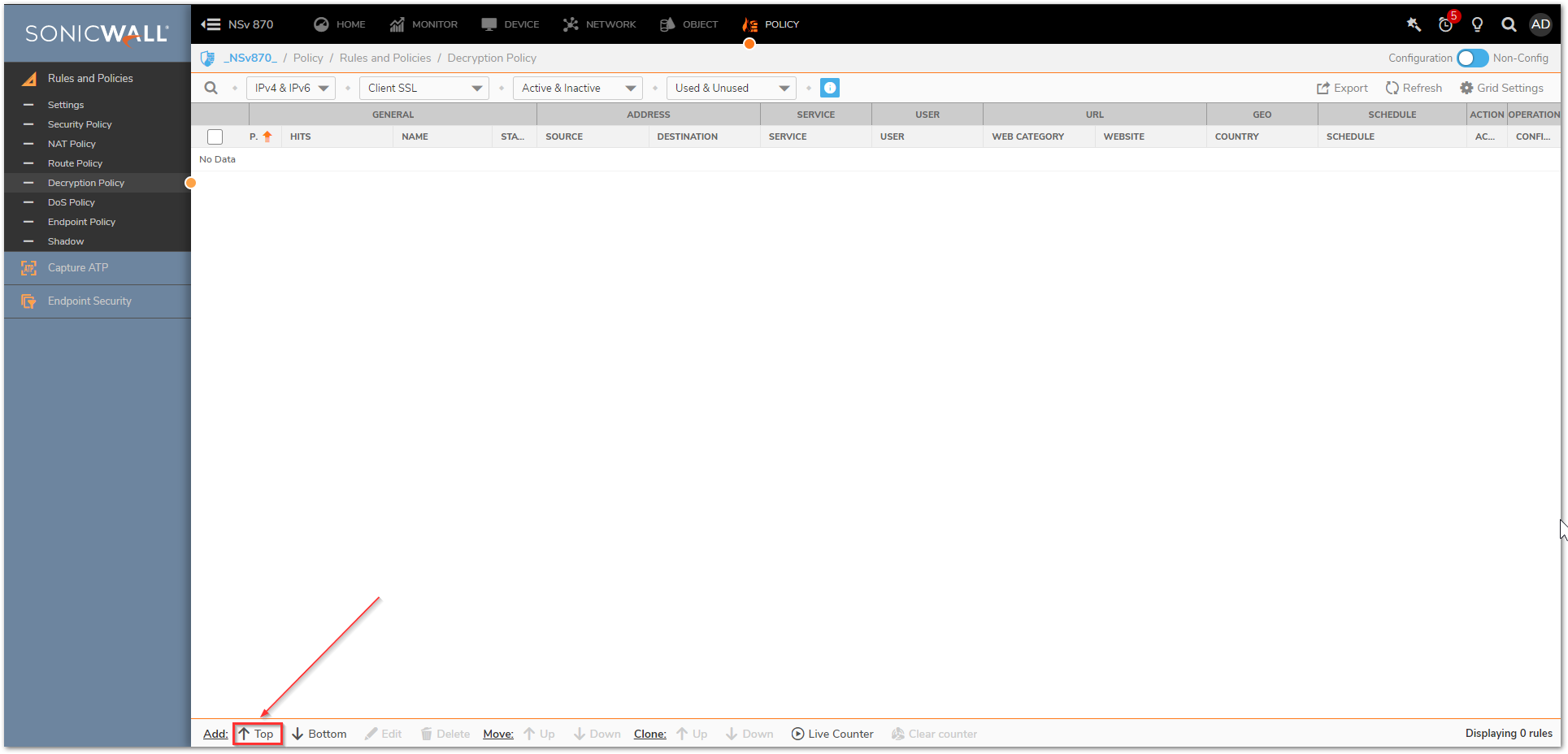
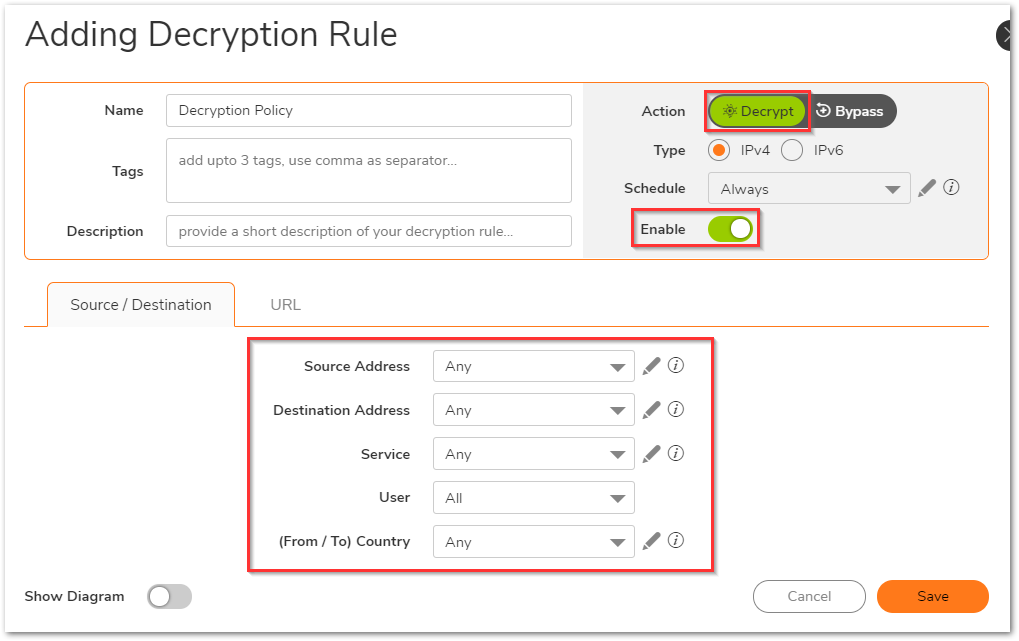
- Select the appropriate source/destination/service or you can leave it all on Any to decrypt all traffic. Make sure that the action is set to Decrypt and the policy is enabled.
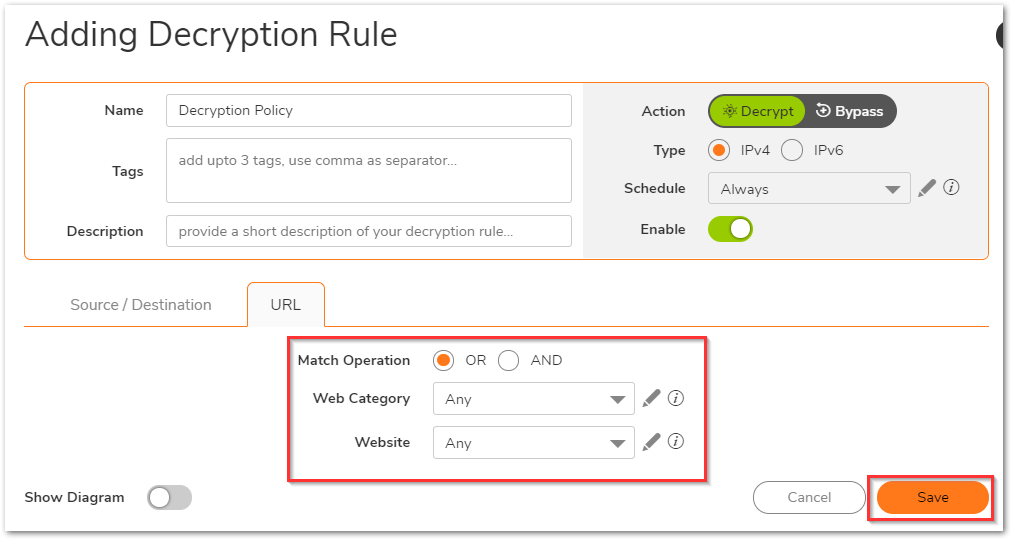
- On the URL tab, you can perform this specific to a web category or the URI list as well. In this example, they are left on Any. Click Save.
Creating a Security Policy
Security Policy ties together the URI list object, Security Rule Action so that we know what action needs to be taken for a specific match. Before an HTTP/HTTPS connection can be made, the end machine would need to perform DNS resolution of the URL. Since we have an implicit deny rule, DNS traffic needs to be allowed as well.
To create the DNS related Security Policy
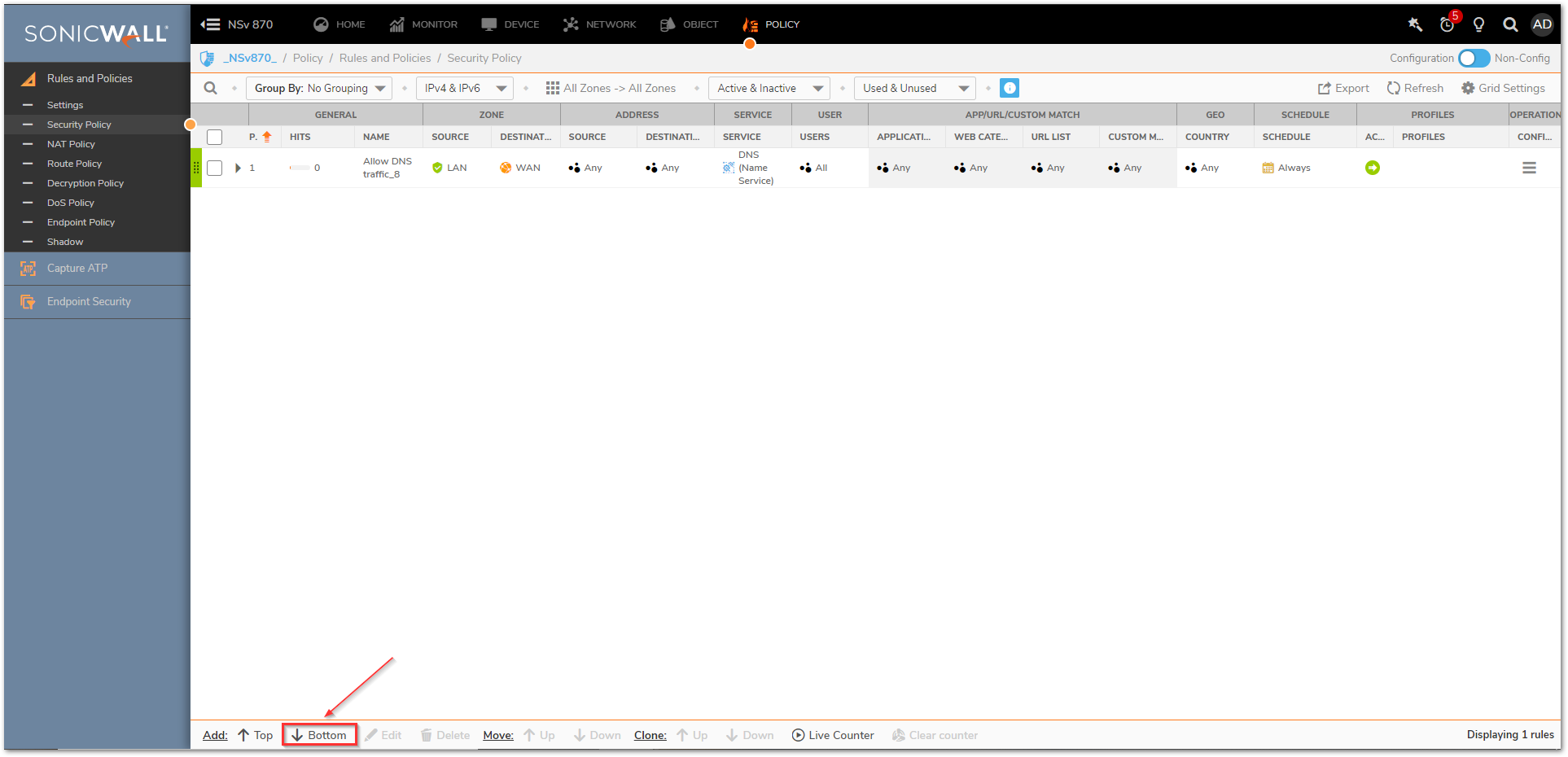
- Navigate to Policy | Rules and Policies | Security policy tab and click on Top at the bottom of the screen. This adds the new Policy at the top of the list. You might need to adjust its priority based on other rules you have.
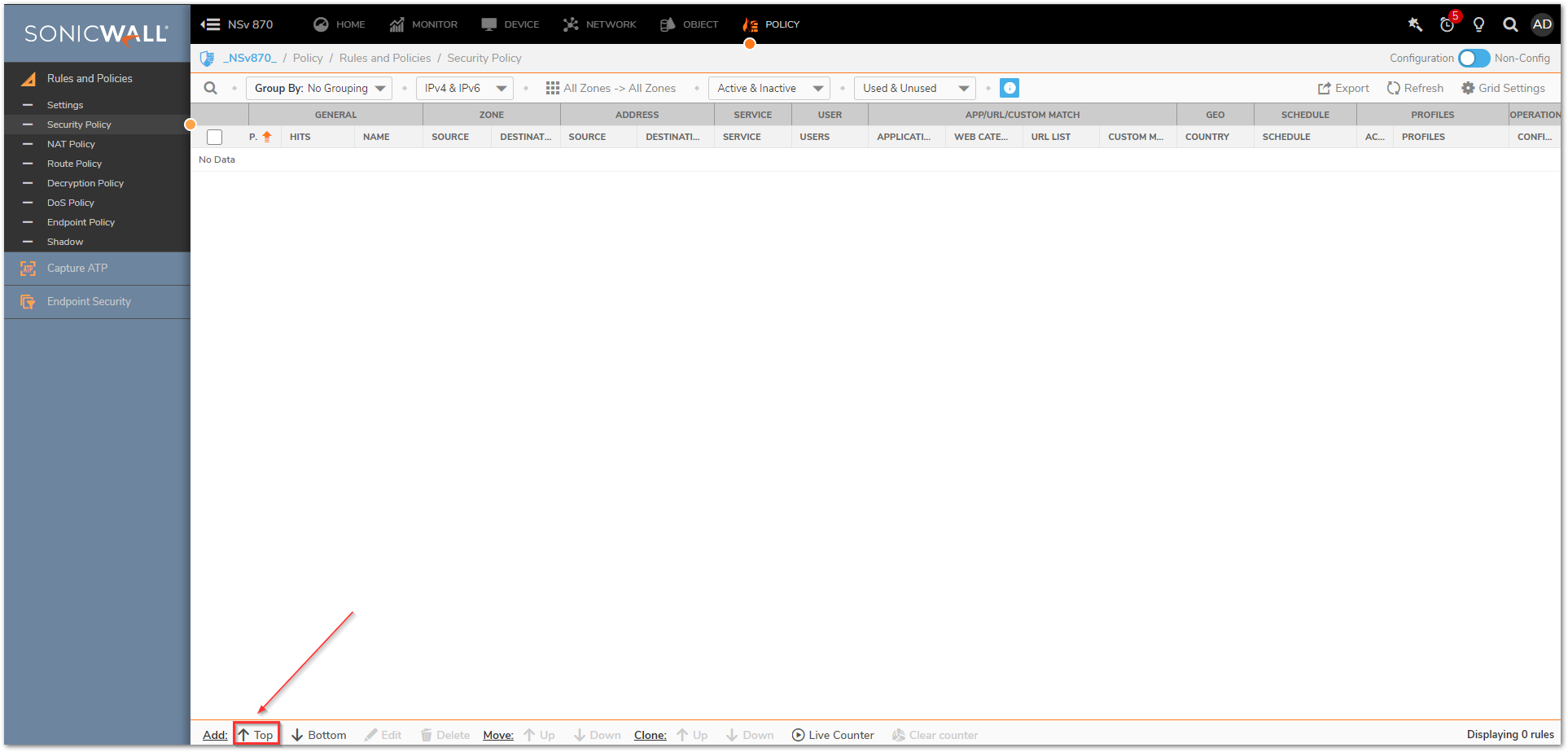
- Mention a relevant name and in the Source/Destination tab, you can select many fields like source/destination zones, address, services and also user, geo-location settings. Select the destination Port/Services as DNS(Name Service).
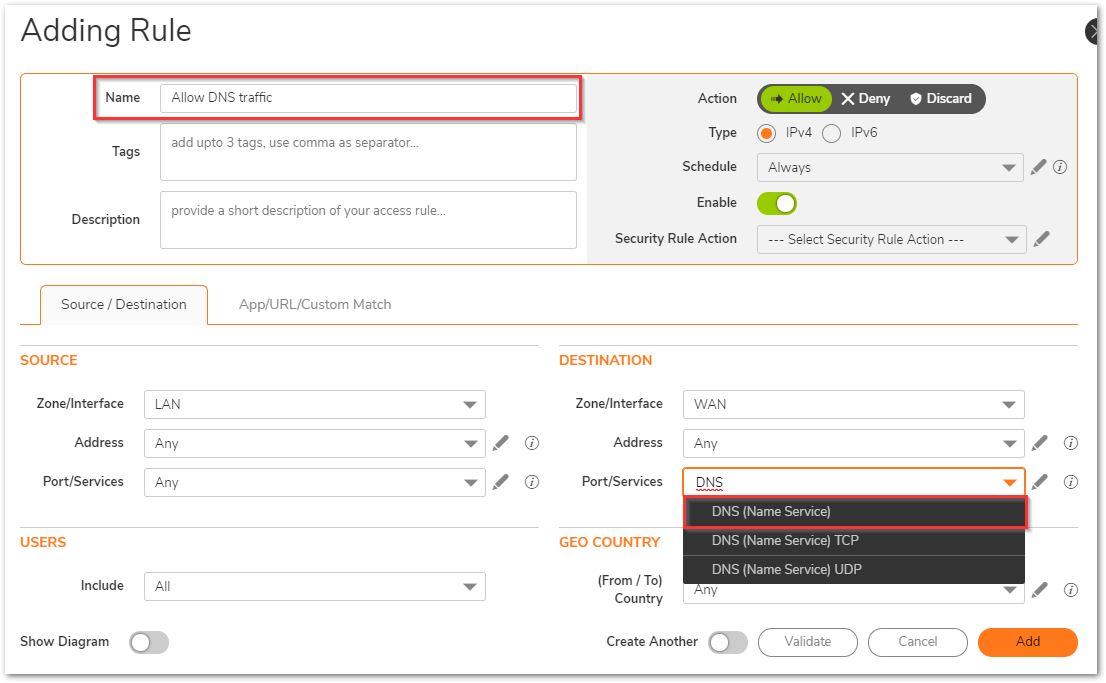
- Under App/URL/Custom Match tab leave everything on defaults.
- Select the Default Profile as the Security rule action. Make sure that the Action is set to Allow and the policy is in enable state. Click on Add.
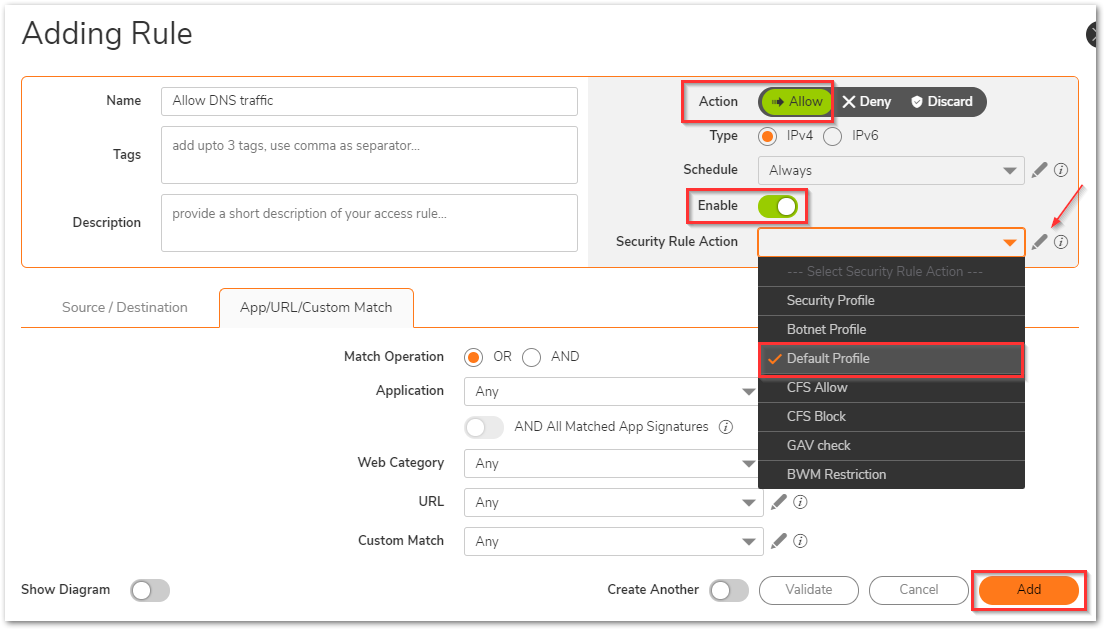
 NOTE: This policy can also be created using the DNS protocol application signature, but this example is configured using the services.
NOTE: This policy can also be created using the DNS protocol application signature, but this example is configured using the services.
To create the allow websites related Security Policy
- Navigate to Policy | Rules and Policies | Security policy tab and click on Bottom at the bottom of the screen. This adds the new Policy at the bottom of the list. You might need to adjust its priority based on other rules you have.
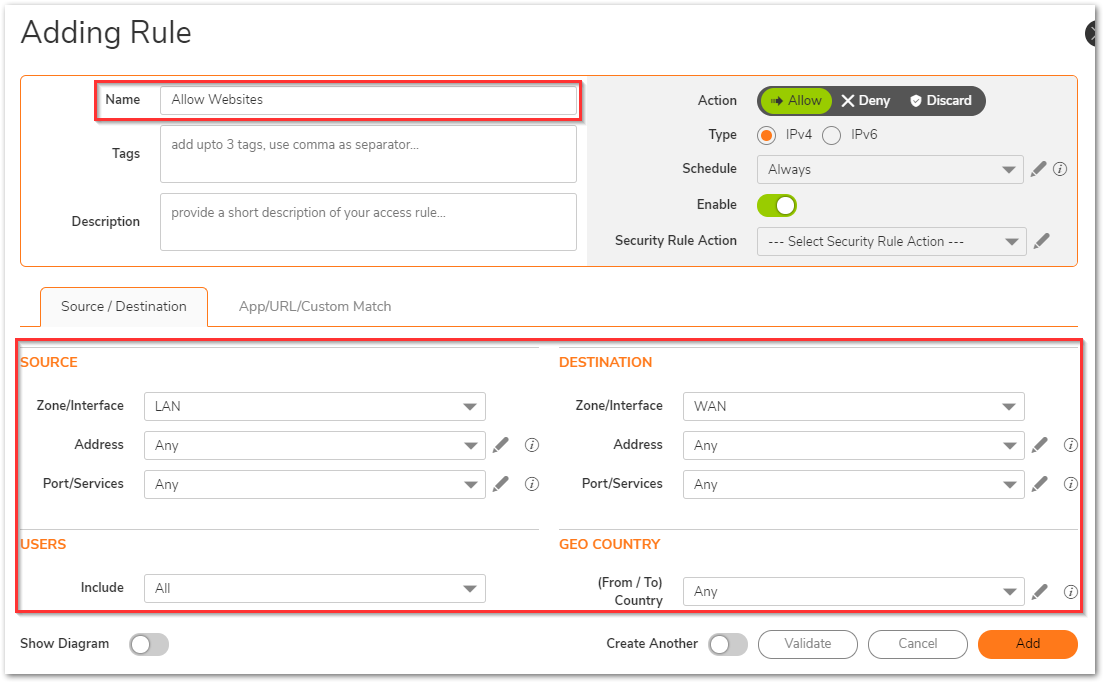
- Mention a relevant name and in the Source/Destination tab, you can select many fields like source/destination zones, address, services and also user, geo-location settings.
- Under App/URL/Custom Match, use the radio button for 'Match Operation' as AND. Also, select the pencil icon to add a new URI List object. For more details on creating URI List objects, refer How to create URI List Objects/Groups on SonicOSX 7.0?
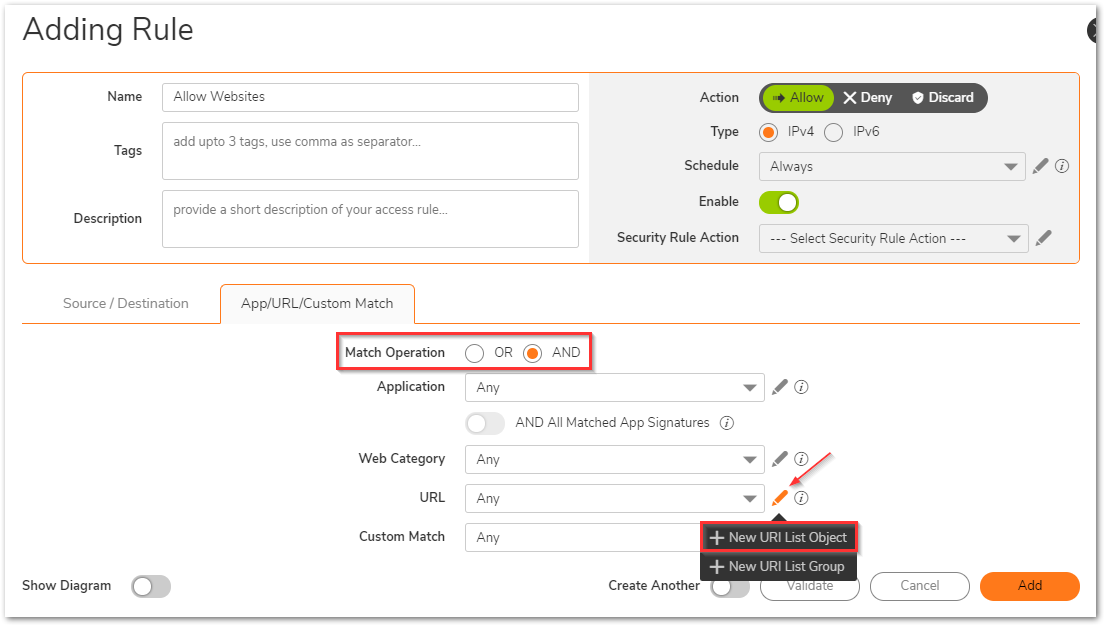
- Under Security rule action dropdown, click on the pencil icon to create a new action.
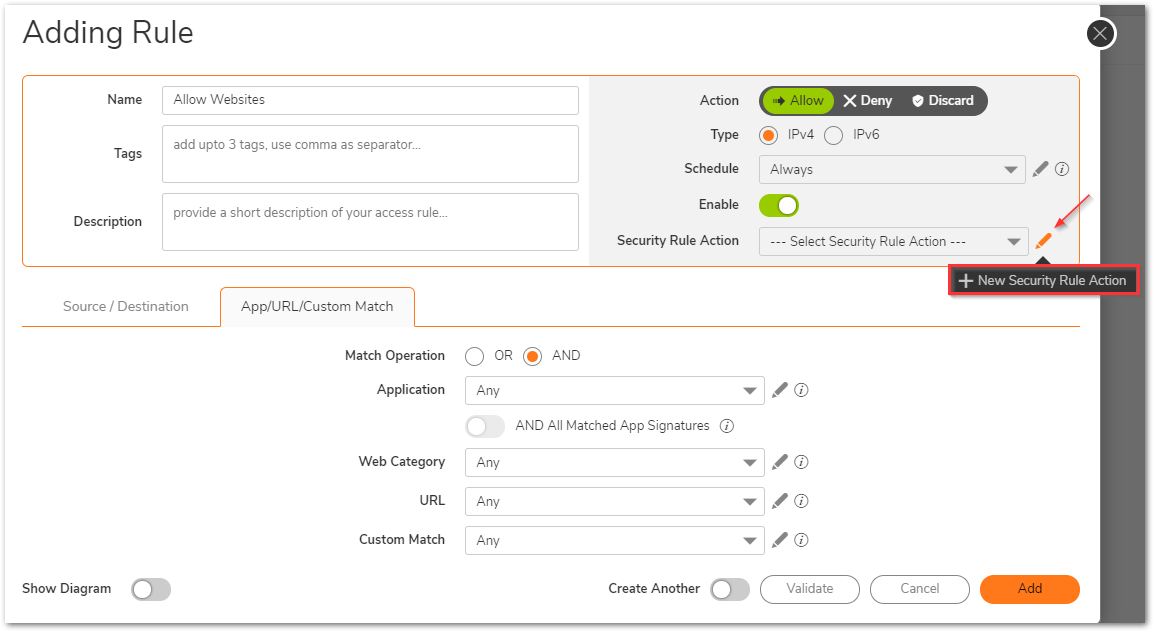
- Give it a relevant name and you can set a lot of other security parameters, but the most important section is Content Filter for this set up. Navigate to Content Filter tab and Enable the toggle button 'Enable Content Filtering'. Also, the Content Filter Action should be set to Allow.
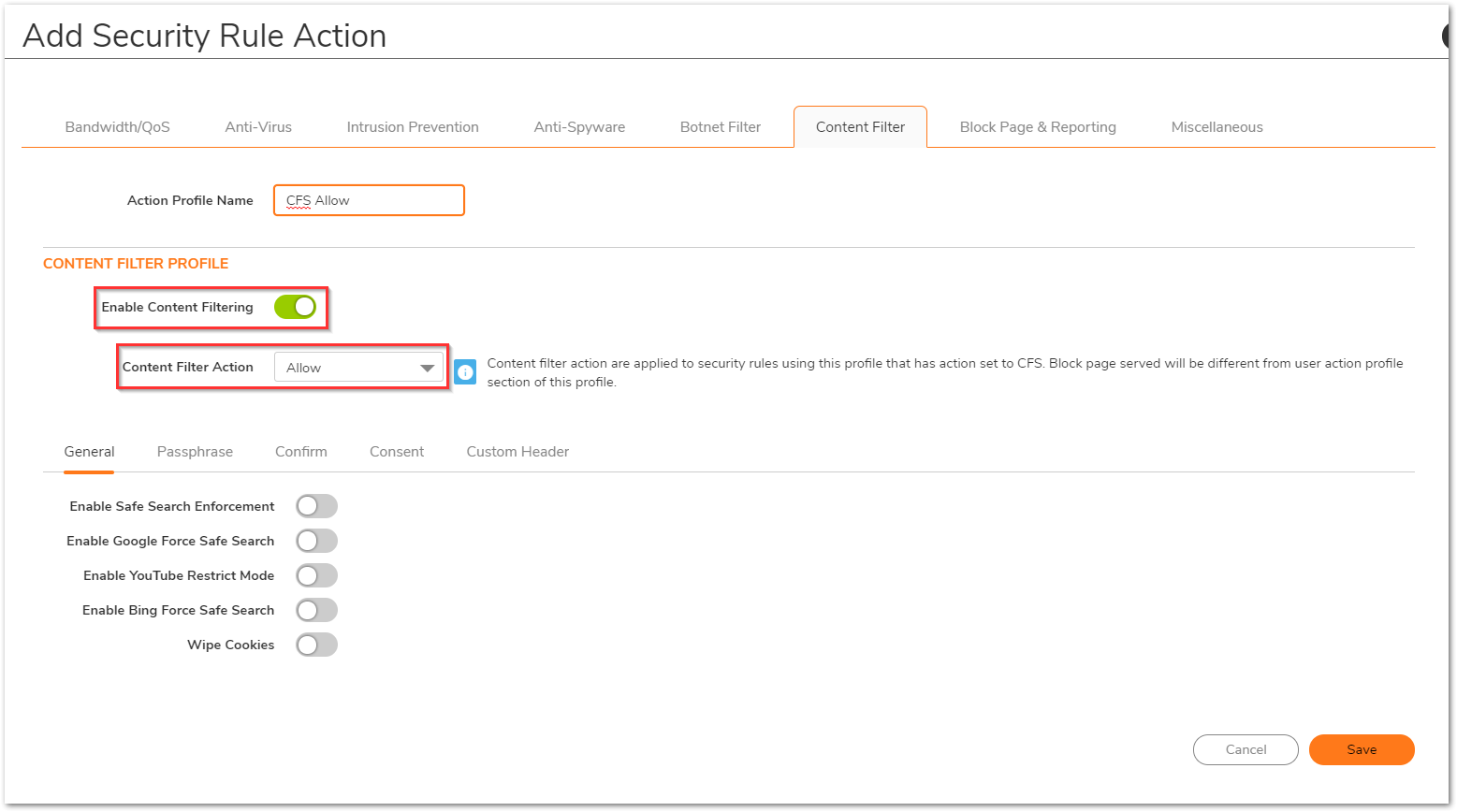
You can also make other additional changes w.r.t. other security features and click on Save once done.- On the Security Policy, make sure that the Action is set to Allow and the policy is in enable state. Click Save.
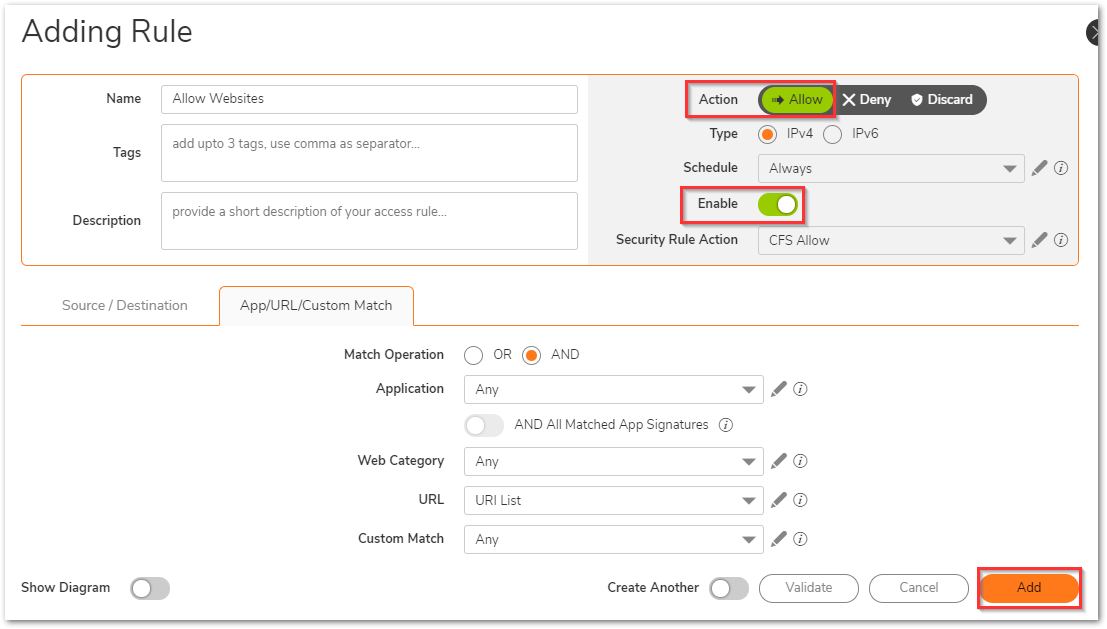
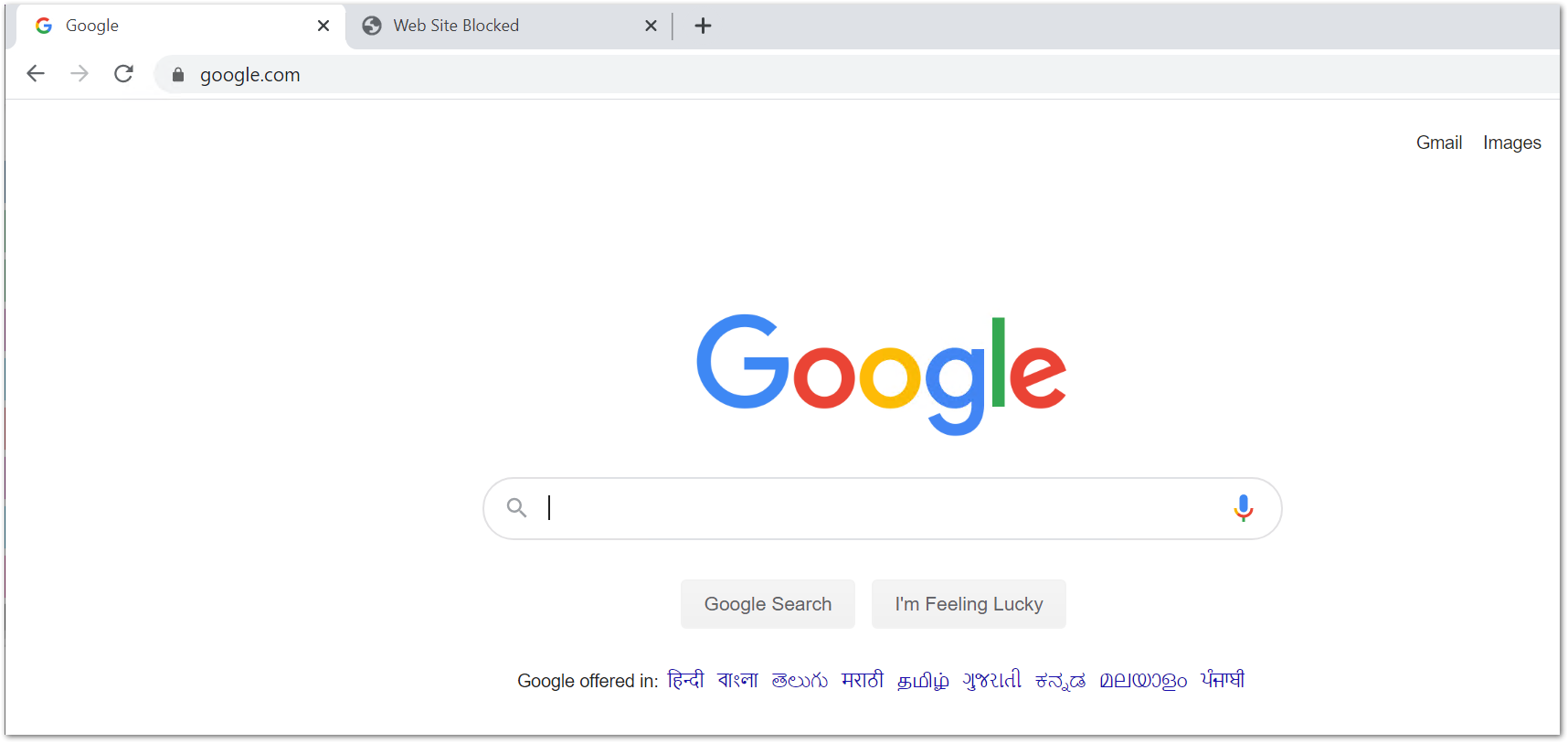
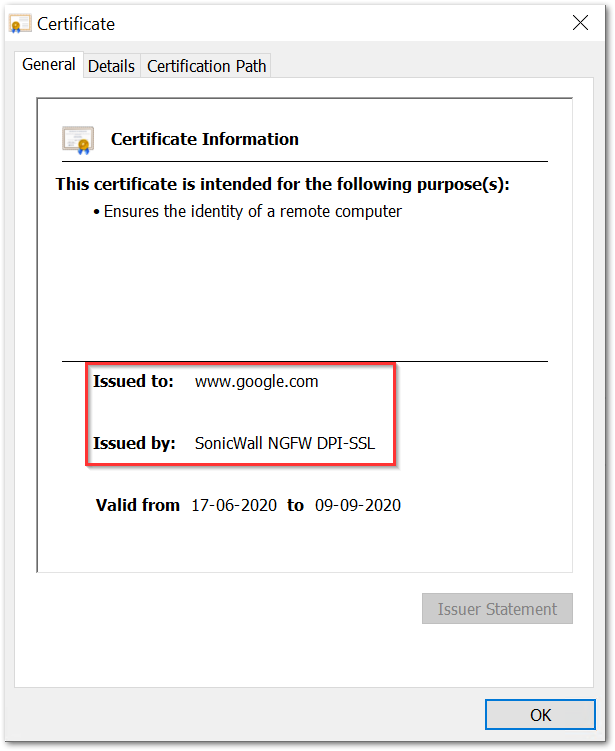
You would be now able to access the websites present on the allowed websites list like google.com and get the blocked page for others. You can also see that the SonicWall DPI SSL certificate shows up for the allowed websites.
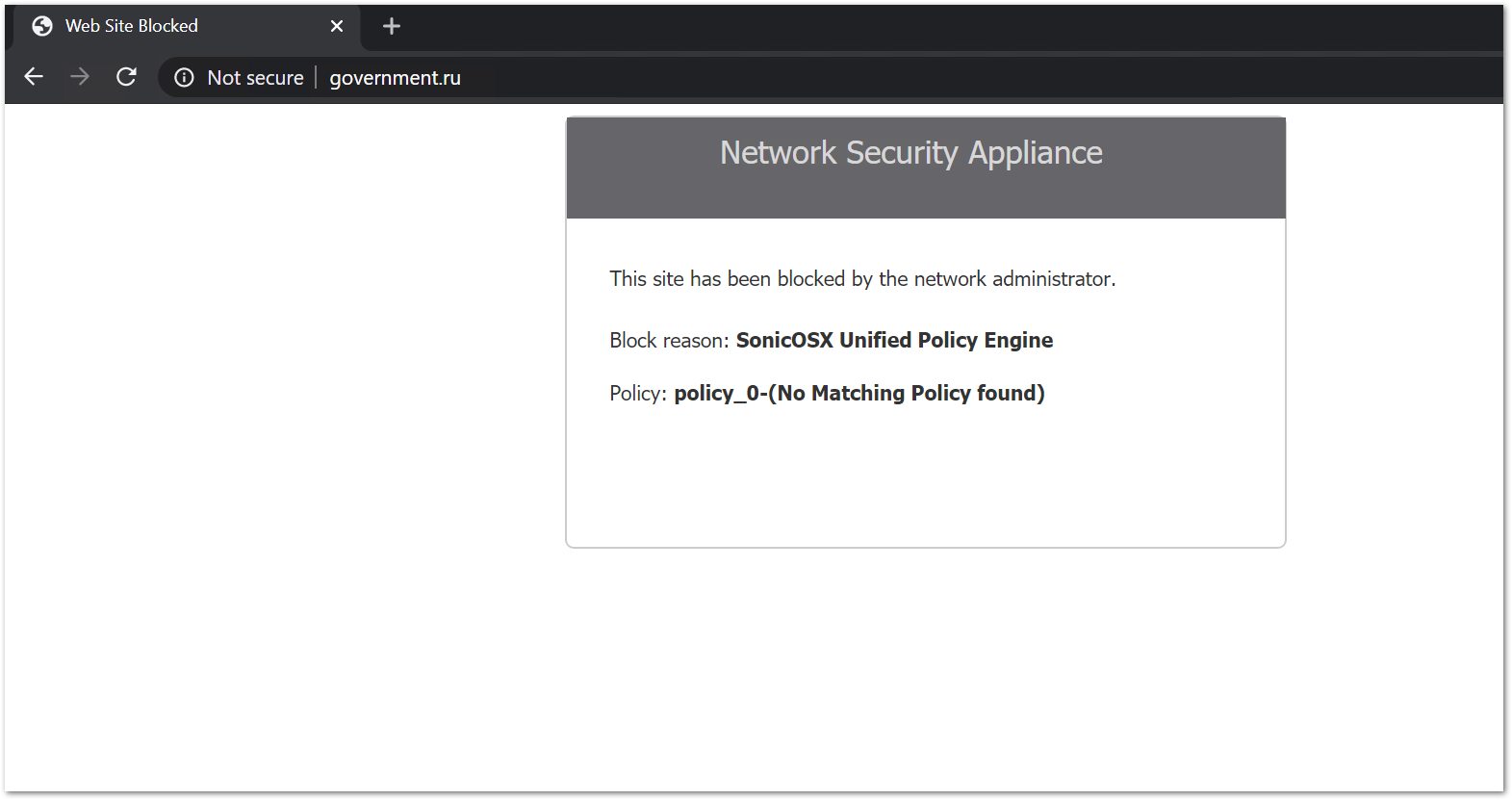
While visiting other websites, the following block page would show up depicting there is no matching policy to allow access to this website.
Related Articles
- Initial and Advanced Firewall Setup for high security environments
- How to setup Active/Standby High Availability on NSSP 13700 appliances?
- How to Create URI List Objects/Groups on SonicOSX 7?






 YES
YES NO
NO